
Kaspersky delves into the alarming activities of the Advanced Persistent Threat (APT) group, ToddyCat, focused primarily on governmental and defense organizations within the Asia-Pacific region.
ToddyCat has been observed stealing sensitive data on an industrial scale, employing a range of sophisticated tools to maintain and automate their access to compromised systems.
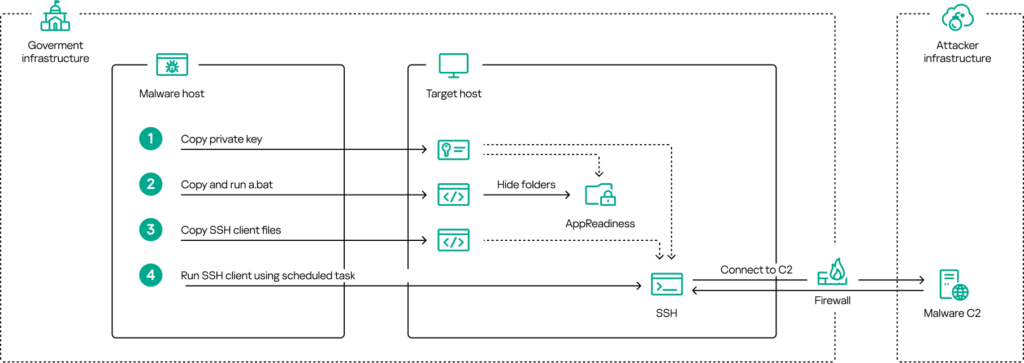
The report, which builds on prior analyses dating October 2023, highlights the methods ToddyCat uses to gain persistent access and extract information. Utilizing tools like reverse SSH tunnels and SoftEther VPN, the group establishes multiple tunnels to ensure continual system access even if one is compromised.
Specific tools and files identified in ToddyCat’s attacks include:
- OpenSSH for Windows with files transferred using SMB (e.g., C:\program files\OpenSSH\ssh.exe)
- SoftEther VPN components like vpnserver_x64.exe cleverly disguised with names like vmtools.exe or kln.exe
- Ngrok and Krong, tools for tunneling and redirecting C2 traffic to cloud infrastructure
- FRP client, a fast reverse proxy used for accessing local servers from the internet
- Cuthead, a new tool ToddyCat utilizes to search and archive documents like PDFs, Word, and Excel files, targeting specific file types and modification dates.
- TomBerBil is another crucial tool in the ToddyCat arsenal, designed to stealthily extract saved passwords and cookies from browsers like Chrome and Edge. The tool masquerades as legitimate software, using filenames such as avpui.exe to evade detection. It operates by identifying and impersonating user processes to decrypt browser data, leveraging the CryptProtectData feature of the DPAPI for encryption.
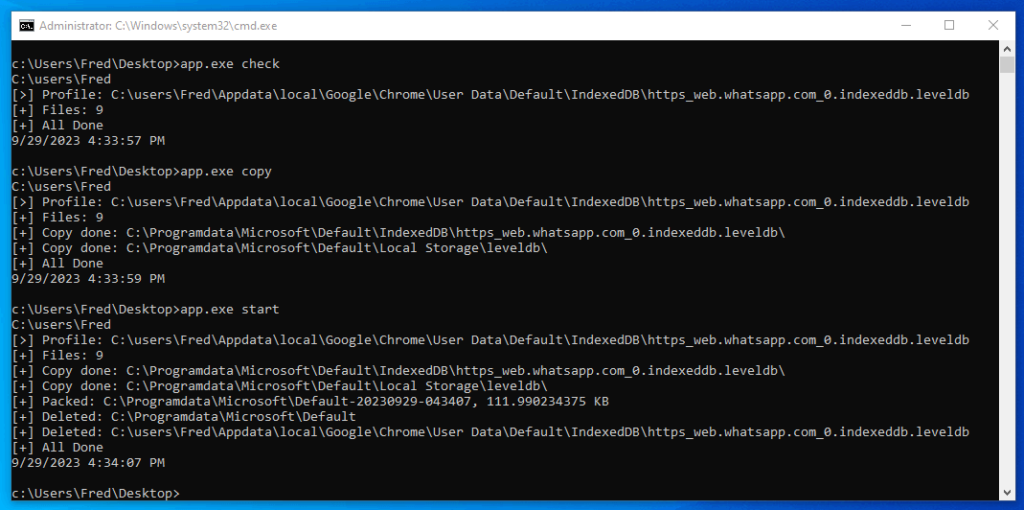
- WAExp, a specialized tool used by ToddyCat to extract WhatsApp data from web browsers. Operating with commands like check, copy, and start, it searches and archives local storage files containing user profiles, chat histories, and session data from Chrome, Edge, and Mozilla.
Kaspersky
One striking aspect of ToddyCat’s operation is their use of legitimate names and locations to disguise their malware, a technique evident in their renaming of files and exploitation of common system directories to evade detection. Additionally, they use advanced methods to hide ownership and permissions of critical folders, essentially locking out users and administrators from detecting or accessing these files.
Kaspersky
Protecting against ToddyCat
Kaspersky provides several recommendations for organizations to safeguard against sophisticated attacks by ToddyCat or similarly sophisticated threat groups. These include:
- Deny-listing suspect IP addresses and cloud services used for traffic tunneling in firewall configurations
- Limiting the range of remote access tools available to administrators and monitor them for signs of misuse
- Following secure password practices and discouraging the storage of passwords in browsers to minimize the risk of theft
- Using the provided indicators of compromise (IoCs) to place targeted blocks on critical systems.
The detailed exposure of ToddyCat’s methods is bound to create operational disruption for the malicious actors. Still, APTs typically refresh their infrastructure and rebound through new TTPs that are challenging to detect and block. Organizations are advised to follow the recommended practices and stay updated with the latest security protocols to protect their sensitive data and infrastructure.







Leave a Reply