
The Scattered Spider cybercriminal group is now aggressively targeting Software-as-a-Service (SaaS) applications and cloud service provider (CSP) environments, aiming to exploit stored data for progression and extortion purposes.
Scattered Spider, also known as Muddled Libra, is a sophisticated cybercriminal group that uses social engineering, phishing, and credential harvesting for financial gain. Notoriously persistent, they target large organizations, demanding millions in ransom, and employ tactics like SIM swapping to intercept SMS-based two-factor authentication.
Their operations have hit major sectors, including telecoms and hospitality, with notable attacks on casino operators like Caesars Entertainment and MGM Resorts. Based possibly in North America, their English fluency and deep understanding of IT infrastructures make them formidable adversaries. Defenses against them require comprehensive security measures and awareness.
As reported today by Unit 42 researchers at Palo Alto Networks, the Scattered Spider's tactics have evolved to leverage the inherent scalability and functionality of CSP services, such as Amazon Web Services (AWS) and Microsoft Azure, to facilitate unauthorized data exfiltration. Despite CSPs' strict terms of service against such actions, Muddled Libra has managed to circumvent restrictions, underscoring the necessity for robust incident response mechanisms and proactive security assessments.
Latest Scattered Spider attacks
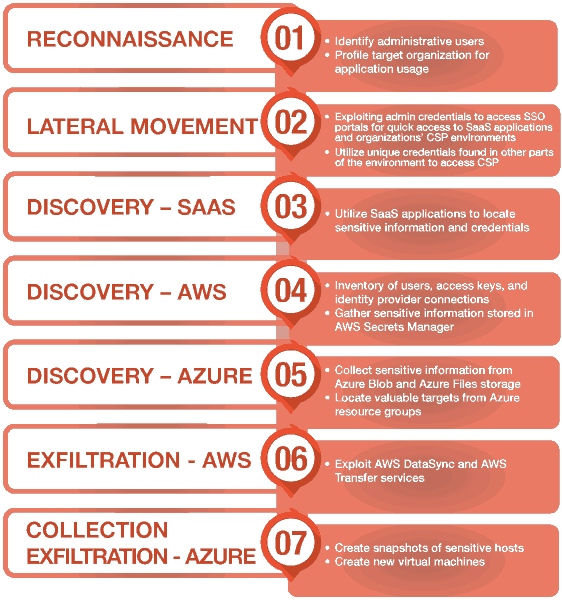
Muddled Libra's operation begins with precise reconnaissance, targeting administrative users through social engineering to gain initial access. This phase, first observed in late 2023 and continuing into January 2024, involves extensive profiling of target organizations to understand their application usage and CSPs.
Unit 42
Notably, their Okta cross-tenant impersonation attacks from late July to early August 2023 exemplify their method of bypassing IAM restrictions and escalating privileges within SaaS applications and CSP environments.
Once inside, Scattered Spider exploits SaaS applications and CSP environments to gather intel, locate credentials, and modify configurations to their advantage. For data exfiltration, they leverage legitimate services like AWS DataSync and AWS Transfer, alongside Azure VM snapshots, to efficiently move data out of the targeted environments.
Unit 42
Defending
To counteract these sophisticated attacks, Palo Alto Networks emphasizes the importance of employing detection, alerting, and mitigation strategies through products like Prisma Cloud. Furthermore, recommendations include hardening Identity Portals, utilizing AWS IAM roles, and Microsoft Entra Privileged Identity Management to restrict long-term access and force frequent reauthentication.
The emergence of Scattered Spider's refined attack vectors underscores the imperative for organizations to reinforce their cloud and SaaS application defenses. For organizations leveraging AWS and Azure, utilizing tools like Amazon GuardDuty, AWS Security Hub, and Azure monitoring capabilities can provide essential insights and security postures against these evolving threats.







Leave a Reply