
A detailed investigation revealed by Mandiant alerts to a series of sophisticated cyberattacks targeting Ivanti Connect Secure VPN appliances.
The findings are part of a series titled “Cutting Edge,” with the latest installment focusing on post-exploitation lateral movement case studies following the exploitation of critical vulnerabilities identified as CVE-2023-46805 and CVE-2024-21887, among others.
Since January 10, 2024, when these vulnerabilities were initially disclosed, Mandiant's efforts have spanned various industry sectors and geographic regions, uncovering the nefarious activities of threat actors, particularly those with connections to China, referred to as China-nexus espionage actors.
These actors have not only exploited the vulnerabilities for initial access but have also demonstrated a deep understanding of Ivanti Connect Secure's functionality to conduct lateral movement within compromised networks. This includes the deployment of both open-source tooling and custom malware families to maintain presence and move stealthily across the victim's environment.
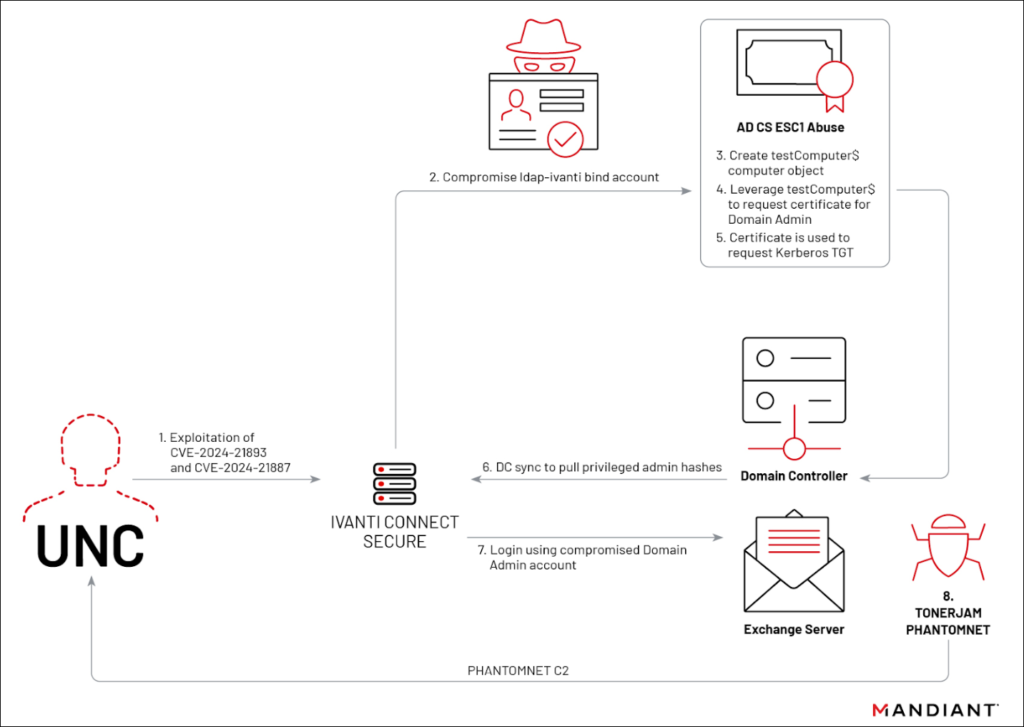
Among the detailed findings, Mandiant highlights the activities of several threat clusters, notably UNC5325, UNC5291, UNC5221, UNC5266, and UNC5330, each employing unique tactics, techniques, and procedures (TTPs). For instance, UNC5221 has been implicated in both pre-disclosure and widespread post-disclosure exploitation of the vulnerabilities, whereas UNC5266's post-disclosure activities involve the deployment of the SLIVER implant framework, a WARPWIRE variant, and a newly identified malware family named TERRIBLETEA.
Mandiant
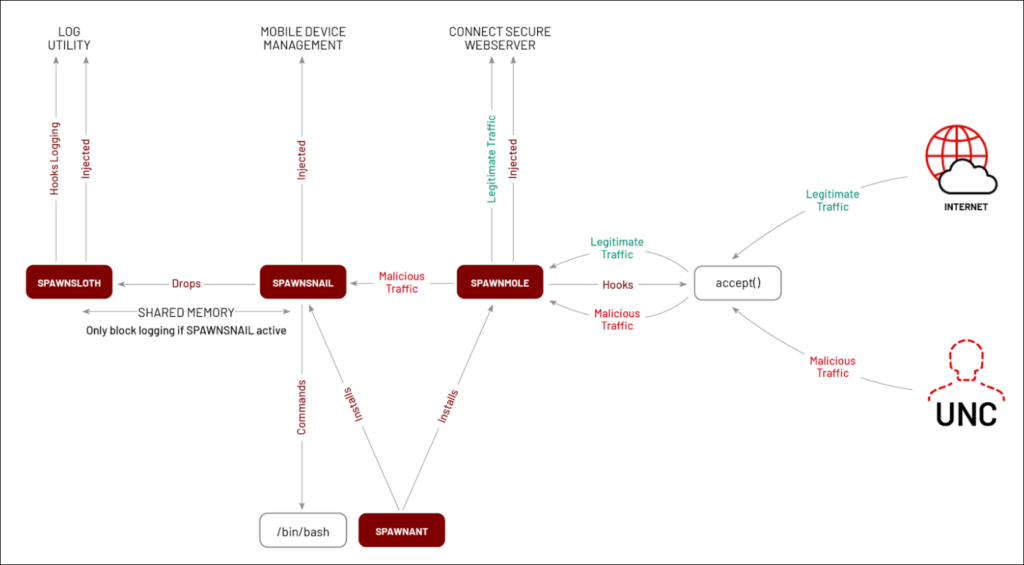
Further analysis provided insight into the sophisticated nature of the attacks, including the use of the SPAWN malware family, consisting of interconnected malware like SPAWNANT, SPAWNMOLE, SPAWNSNAIL, and SPAWNSLOTH, designed to establish a stealthy and persistent backdoor on compromised appliances. Mandiant also discovered a new web shell, dubbed ROOTROT, used by threat actors to maintain access to compromised systems.
Mandiant
The implications of these findings are significant, underscoring the criticality of edge appliances as targets for adversaries seeking to gain initial access to organizational networks. Ivanti has since released patches for the vulnerabilities and an enhanced external integrity checker tool (ICT) to aid in detecting attempts at malware persistence. Mandiant strongly advises customers to apply these patches and follow the recommended mitigation strategies to protect against further exploitation.
The relentless pursuit of vulnerabilities by threat actors, especially those impacting edge appliances, leaves organizations no margins for delays in patching. Mandiant concludes its report warning that it continues to see China-nexus hackers exploiting zero-day and N-day vulnerabilities, followed by a broad range of activities, including the deployment of off-the-shelve and custom malware tools optimized specifically for each operation.






Leave a Reply