
A report by Lutra Security uncovers a vulnerability in HTML emails, dubbed “Kobold Letters,” which allows email content to change when forwarded, posing a risk for phishing attacks.
This issue primarily affects Mozilla's Thunderbird and Microsoft's Outlook on the Web, while other clients like Gmail being less susceptible due to stripping styling on forwarding.
The vulnerability exploits the CSS styling capabilities of email clients, allowing malicious actors to craft emails that change appearance once forwarded. Named after the elusive sprites of mythology, these “Kobold Letters” remain invisible or transform based on their viewing context, making them a potent tool for phishing attacks.
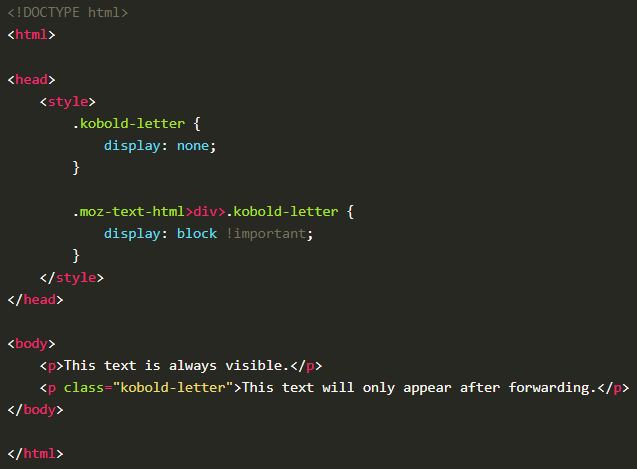
The vulnerability primarily relies on the fact that most email clients and webmailers support HTML email, thus allowing CSS to manipulate the visual presentation of emails based on their position in the Document Object Model (DOM). For instance, an email may appear innocuous when directly viewed but reveal a phishing attempt once forwarded without the original sender being aware. This technique leverages the changing DOM structure when an email is forwarded, applying specific CSS rules to hide or reveal certain elements.
Lutra Security
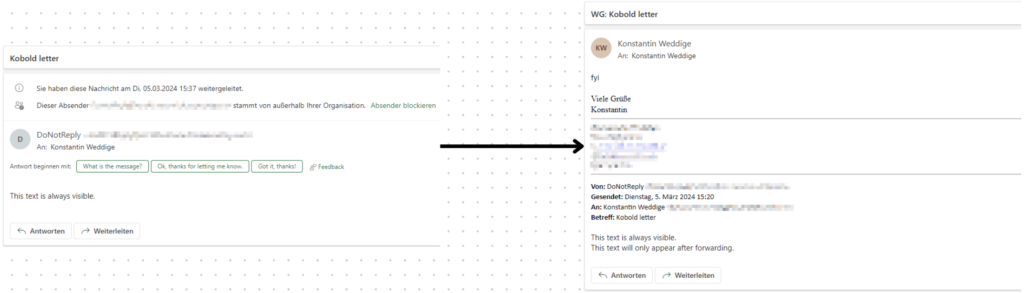
Notably, the investigation highlights how this issue affects major email clients like Mozilla's Thunderbird and Microsoft's Outlook on the Web (OWA), with detailed proof of concept for each. Thunderbird, for example, wraps emails in specific tags that can be targeted by CSS selectors to hide or show content based on its position in the forwarded email chain. Similarly, OWA's handling of emails, although slightly more complex due to its webmail nature, does not impede the execution of such attacks.
Lutra Security
While Google's Gmail strips all styling from emails when forwarding, limiting the scope of this vulnerability, the fundamental issue persists across multiple platforms. Prior reports have touched on related vulnerabilities, but the “Kobold Letters” research casts a wider net, examining the problem across several email clients to underscore the broader implications for HTML email security.
The underlying challenge in mitigating these risks is the delicate balance between security and functionality. Disabling HTML emails or restricting their capabilities could significantly impact the user experience and the visual quality of emails, affecting everything from corporate newsletters to personal correspondence. This highlights the importance of finding a balanced solution that ensures both security and functionality.
Lutra Security says it reported the issue to the impacted vendors on March 5, 2024, but there has been no response indicating a fix is on the way. Microsoft even marked the report as closed on March 26, 2024, implying it is not planning to take any remediation action.






Leave a Reply