
Researchers have found multiple flaws in the Mavic 3 series of drone products, which could allow unauthorized actors to hijack the drone and exfiltrate sensitive data from it.
DJI is a leading drone manufacturer known for its high-quality products, while the Mavic 3 series is one of the firm's flagship lines, particularly popular for its advanced features, including superior camera quality, long flight times, and extensive range. Appealing to both hobbyists and professionals, it is a popular choice in the global market.
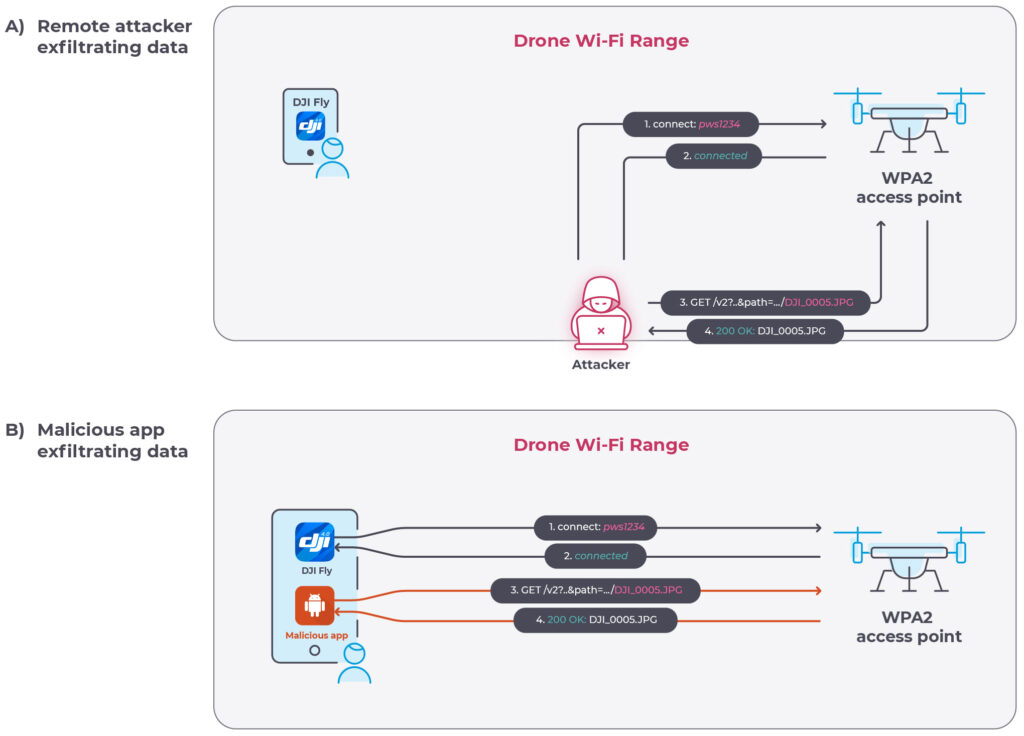
In a recent in-depth vulnerability analysis conducted by Nozomi Networks Labs, the DJI Mavic 3 Series drones' security framework was scrutinized, revealing critical vulnerabilities within its QuickTransfer Mode protocol. This protocol, primarily designed for rapid media file transfer to users' mobile devices, was identified as a potential weak link that could be exploited for unauthorized data exfiltration.
The analysis discovered nine vulnerabilities, all of which required user interaction to activate. DJI, upon review, has resolved seven of these issues, leaving two disputed as not requiring fixes. The vulnerabilities revolve around the Wi-Fi-based QuickTransfer Mode, with the investigation marking certain DJI Mavic 3 models for firmware updates to mitigate these security concerns.
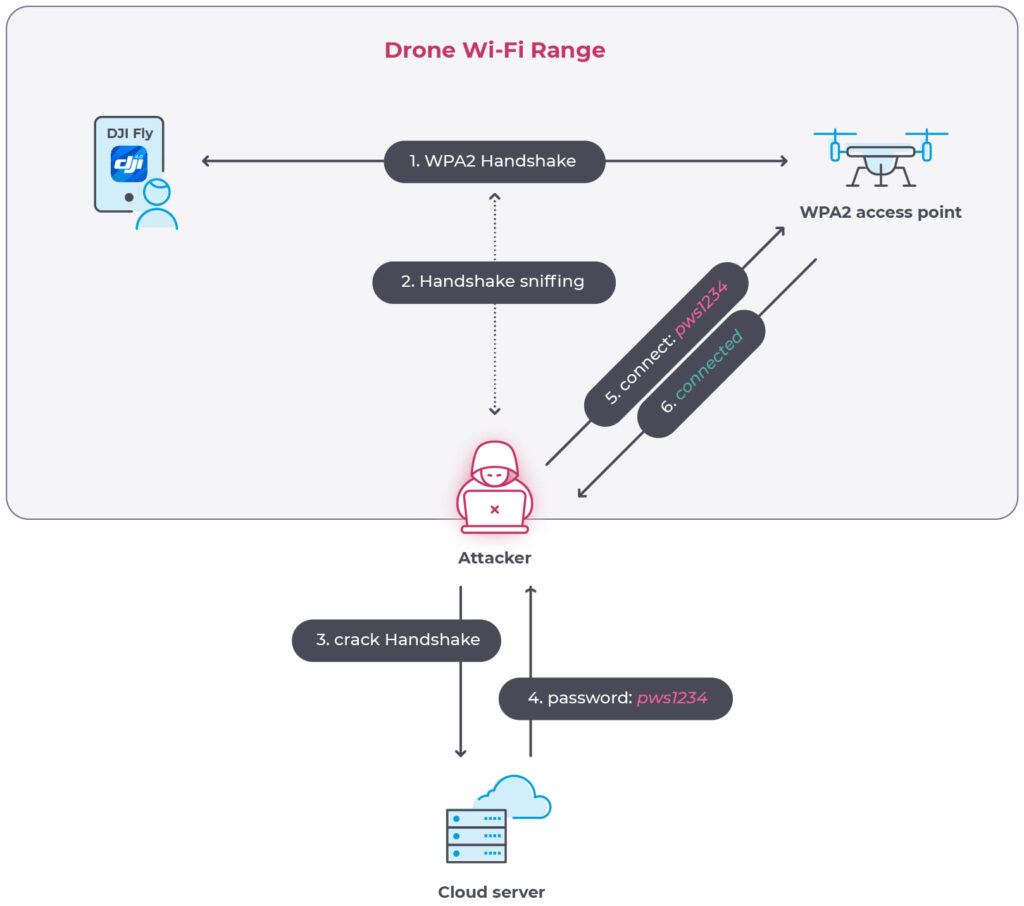
One significant vulnerability identified concerns the method of Wi-Fi password generation, which, due to its predictability, could allow attackers to easily crack the password, gaining unauthorized access to the drone. This vulnerability, designated CVE-2023-6951, exposes the drone to potential unauthorized interactions that could compromise its security.
Another aspect of the drone's system scrutinized was the FTP service, designed for diagnostic purposes but found to be accessible without authentication, presenting a potential point of exploitation. However, due to its limited impact, DJI has disputed the necessity of addressing this vulnerability, which has been assigned CVE-2023-6950.
Another point of concern emerged in the vtwo_sdk service, integral for maintenance and operating with root privileges. Vulnerabilities within this service could allow for arbitrary code execution or information leaks.
Furthermore, an unauthenticated API within the drone's HTTP service was identified, enabling the potential for unauthorized media file downloads. This vulnerability, marked as CVE-2023-6949, highlights the risk of data exfiltration, especially when combined with the QuickTransfer Mode's Wi-Fi password vulnerability.
DJI has issued firmware updates for the Mavic 3 series to address identified vulnerabilities. Users should update their drones to the latest firmware to safeguard against unauthorized access and data leaks. The following firmware versions resolve the mentioned vulnerabilities, except for the two that DJI decided not to address this time:
- Mavic 3 Pro: v01.01.0300
- Mavic 3: v01.00.1200
- Mavic 3 classic v01.00.0500
- Mavic 3 Enterprise v07.01.10.03
- Matrice 300 v57.00.01.00
- Matrice M30 V07.01.0022
- Mini 3 Pro v01.00.0620
The broader implications of these flaws extend beyond individual users, affecting organizations that rely on drone technology for critical operations. The potential for unauthorized control or access to sensitive information underscores the need for comprehensive risk management and security measures. DJI's market dominance makes the implications of these findings significant, urging users and organizations to update their devices to the latest firmware versions to mitigate these security risks.







Leave a Reply