
Data from 700 million LinkedIn users has been put up for sale online, making this one of the largest LinkedIn data leaks to date. After analyzing the data and making contact with the seller, we have updated this article with more information, including how the data was obtained and the possible impact on LinkedIn users.
UPDATE: LinkedIn has confirmed via email to RestorePrivacy that the data was obtained from their servers, as well as from other sources. And contrary to some reports, LinkedIn is NOT denying that data was harvested from their servers. They point out, however, that some data was also obtained from other sources.
Many people trust LinkedIn with all sorts of private data, hoping and trusting that the information remains in safe hands. But is this trust warranted? So far in 2021, we have already seen two separate incidents where bad actors have exploited the professional networking platform to harvest vast amounts of user data.
The implications of this are far-ranging, from identity theft to phishing attacks, social engineering attacks, and more. Before we dive into the consequences of this leak, let\'s first examine what happened.
What happened exactly?
On June 22nd, a user of a popular hacker forum advertised data from 700 Million LinkedIn users for sale. The user of the forum posted a sample of the data that includes 1 million LinkedIn users. We examined the sample and found it to contain the following information:
- Email Addresses
- Full names
- Phone numbers
- Physical addresses
- Geolocation records
- LinkedIn username and profile URL
- Personal and professional experience/background
- Genders
- Other social media accounts and username
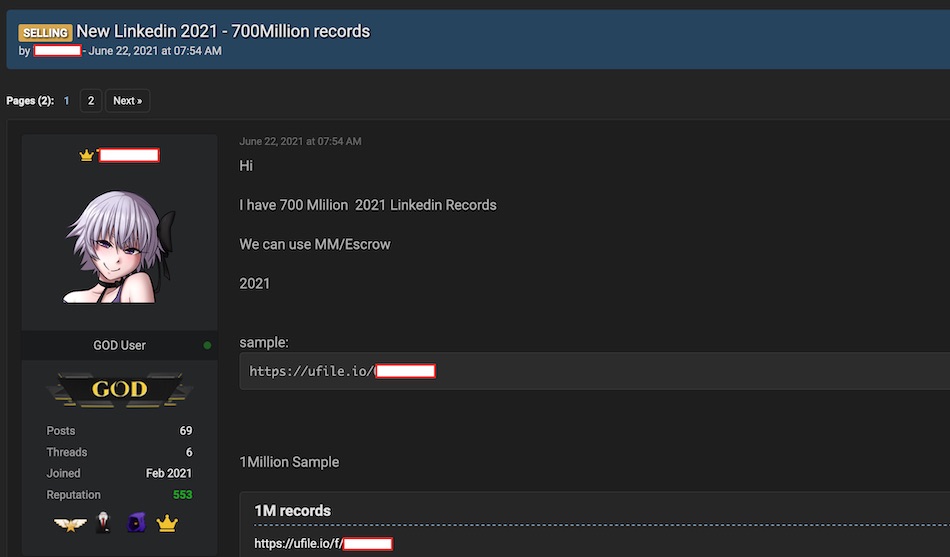
The user claims that the complete database contains the personal information of 700 Million LinkedIn users. Since LinkedIn has 756 million users, according to its website, this would mean that 92% of all LinkedIn users can be found in these records.
Below is a small section of the sample we examined to show you how much information one record can contain:
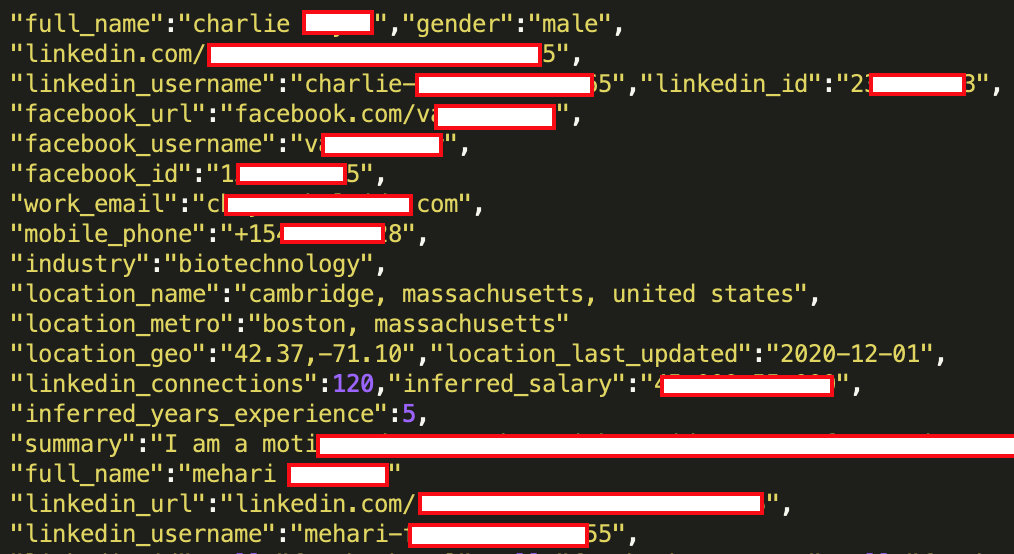
Based on our analysis and cross-checking data from the sample with other publicly available information, it appears all data is authentic and tied to real users. Additionally, the data does appear to be up to date, with samples from 2020 to 2021.
While we did not find login credentials or financial data in the samples we examined, there is still a treasure trove of information for bad actors to exploit for financial gain, as we\'ll explain more below.
How was the data obtained?
We reached out directly to the user who is posting the data up for sale on the hacking forum. He claims the data was obtained by exploiting the LinkedIn API to harvest information that people upload to the site.
Below is one interaction we had with the threat actor on Telegram. You can see that he is asking $5,000 for the complete data set, and stating that the data was acquired through the LinkedIn API.
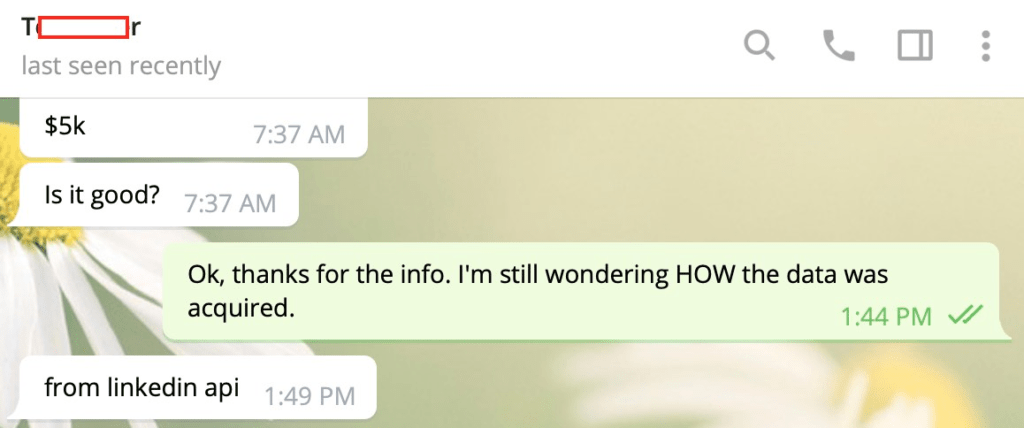
However, LinkedIn has emailed us an explanation, stating that not all of the data could have been acquired through the LinkedIn API. Instead, some of the data likely came from other sources.
LinkedIn has even issued a statement here, where they note that their “initial investigation has found that this data was scraped from LinkedIn and other various websites.”
Everything remains up for sale at this time.
Official response from LinkedIn
We have also reached out to LinkedIn for comment on this latest data leak. They have confirmed that the data was scraped from their servers, as well as other sources, but are also claiming that \”no private LinkedIn member data was exposed.\” And note that the definition of \”private data\” is surely subjective.
Our teams have investigated a set of alleged LinkedIn data that has been posted for sale. We want to be clear that this is not a data breach and no private LinkedIn member data was exposed. Our initial investigation has found that this data was scraped from LinkedIn and other various websites and includes the same data reported earlier this year in our April 2021 scraping update.
– LinkedIn\'s full statement can be found here.
It is important to note that LinkedIn is not denying that data was harvested from their servers. They are simply pointing out that:
- Some of the data was also obtained from \”other various websites\”.
- They do not consider your LinkedIn data that was exposed to be \”private\”.
So what is the definition of “private data” and what expectation of privacy do you have when you upload data to LinkedIn?
Possible impact of this latest LinkedIn data leak
While this latest LinkedIn leak did not contain any financial records or login credentials, there are still serious consequences. This is because it puts 700+ million people at risk of:
- identity theft
- phishing attempts
- social engineering attacks
- hacked accounts
Cybercriminals can use the information found in the leaked files with other data in order to create full detailed profiles of their potential victims. Additionally, bad actors can use the available data, particularly usernames, emails, and personal information, to gain access to other accounts.
Above all else, this information exposes LinkedIn users to a higher risk of exploitation by bad actors.
And once your private data is leaked, there\'s no getting it back.
Should companies be financially liable when your data is exposed?
This leads us to an interesting question. Should companies be held liable when user data is exploited by bad actors?
In this specific case, it does not appear that LinkedIn servers were hacked or there was a full “breach” in the traditional sense of the term. Instead, however, the data was harvested through LinkedIn's own API (application program interface) by threat actors.
How much privacy should one really expect on a social networking site?
When others have your data, it puts you at risk
We've said it before and we'll say it again: any business, individual, or entity that has control over your private data puts you at risk. Whether this risk is minimal or vast depends on the data, who is securing it, and the consequences of it being lost.
To minimize this risk, you need to limit the amount of data that is available to others.
This could include getting off of all social networks entirely, or limiting the information you share. Using products and services that don't harvest your personal information for profit is also crucial. We have reviewed some of the best options with:
- Secure browsers that respect your privacy and don\'t collect your data for advertising networks
- Secure and private email services that don't sell access to your inbox or scan your emails and attachments
- Private search engines that respect your privacy
And of course, you should remain vigilant to all potential attacks while continuing to safeguard your personal information.






Leave a Reply