
Malwarebytes researchers have uncovered the “zqxq” campaign, a large-scale cyberattack targeting over 2,800 websites through malicious JavaScript injections. This campaign exploited vulnerabilities on high-traffic platforms, redirecting visitors to malicious domains hosting phishing pages, exploit kits, or malware payloads. Among the affected sites was GroupGreeting[.]com, a popular e-card service used by thousands of enterprises, which serves as a case study for understanding the broader threat.
How the “zqxq” campaign works
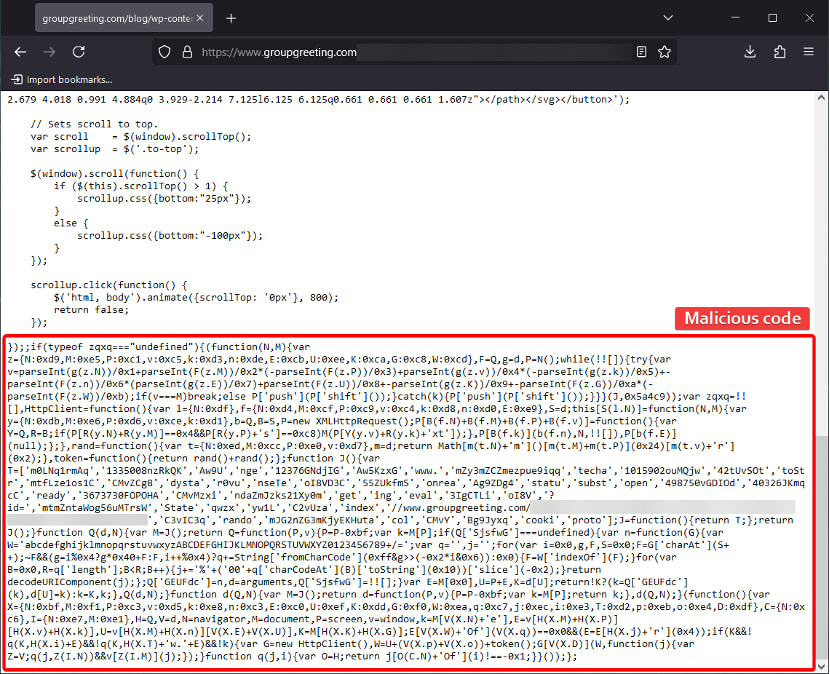
The attack leveraged obfuscated JavaScript to infiltrate websites and silently execute malicious actions. Key functions of the script include:
- Redirecting users: The JavaScript generated randomized, tokenized URLs to redirect visitors to external malicious domains. These domains hosted phishing pages, exploit kits, or malware like info-stealers and ransomware.
- Evasion techniques: Conditional checks on user properties, such as cookies or browser history, allowed the script to avoid reinfecting the same users or triggering repeated alerts, minimizing detection.
- Payload retrieval: Using functions like XMLHttpRequest, disguised as HttpClient, the script fetched additional malicious code or delivered secondary payloads to targeted devices.
- Traffic distribution: The malware acted as part of a Traffic Direction System (TDS), funneling traffic based on user attributes, such as geographic location or device type, to maximize infection success.
These tactics illustrate how attackers could simultaneously compromise multiple sites while maintaining a low profile.
GroupGreeting among the compromised
GroupGreeting, a platform with over 25,000 workplace clients, was an example of how the campaign exploited high-traffic sites. Known for facilitating group e-cards for occasions like holidays and workplace celebrations, the site experienced a significant increase in usage during the holiday season, making it an ideal target.
The malicious JavaScript embedded on GroupGreeting redirected users to external domains hosting phishing schemes or malware downloads. Though the company responded swiftly to remove the infection, the attackers’ use of deeply hidden and obfuscated code demonstrated the resilience of the campaign.
Malwarebytes
The “zqxq” operation did not rely on spreading from one site to another but systematically targeted vulnerabilities across thousands of websites. Many of these were built on outdated CMS platforms like WordPress and Joomla or relied on unpatched plugins, which attackers exploited to inject malicious JavaScript.
The compromised websites shared a common outcome: users were redirected to malicious domains, putting them at risk of credential theft, malware infections, or worse. The campaign’s scale and coordination suggest a high degree of automation in identifying and exploiting site vulnerabilities.
To defend against such attacks, website owners must ensure all CMS platforms, plugins, and themes are updated to their latest version, use file integrity checking tools, and analyze traffic for anomalous activity.







Leave a Reply