
A security researcher recently uncovered an unsecured Microsoft ServiceNow instance, which allowed access to extensive sensitive internal data, including employee email addresses, support ticket transcripts, and attachments.
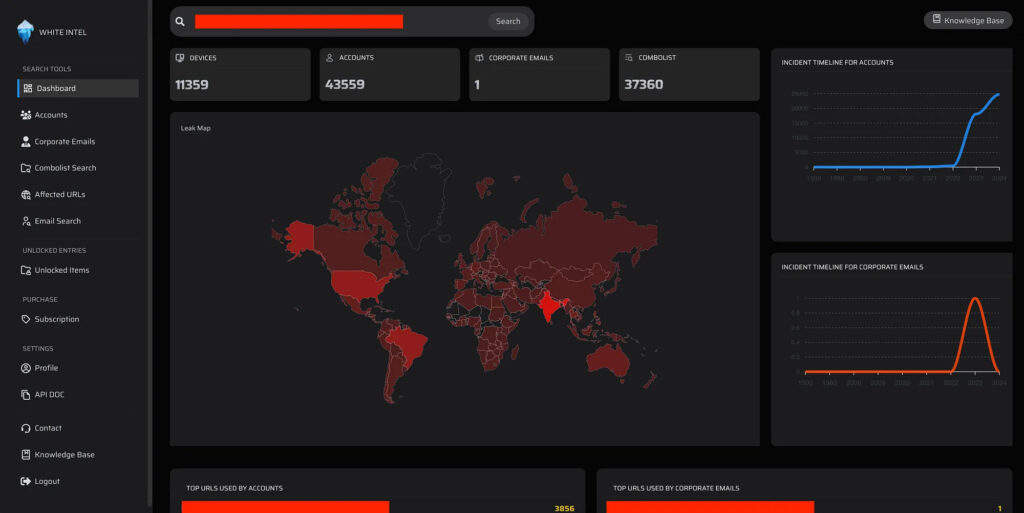
The researcher, writing under the alias Moblig, utilized a tool called WhiteIntel, a search engine specialized in tracking data breaches involving “infostealers” — malware that harvests credentials and sensitive information from infected systems.
medium.com | @moblig
Infostealers often capture saved login details from browsers on unprotected personal devices that corporate employees may use to access company infrastructure. When Moblig searched for instances tied to Microsoft domains, the tool revealed a single compromised credential that provided access to Microsoft’s ServiceNow instance.
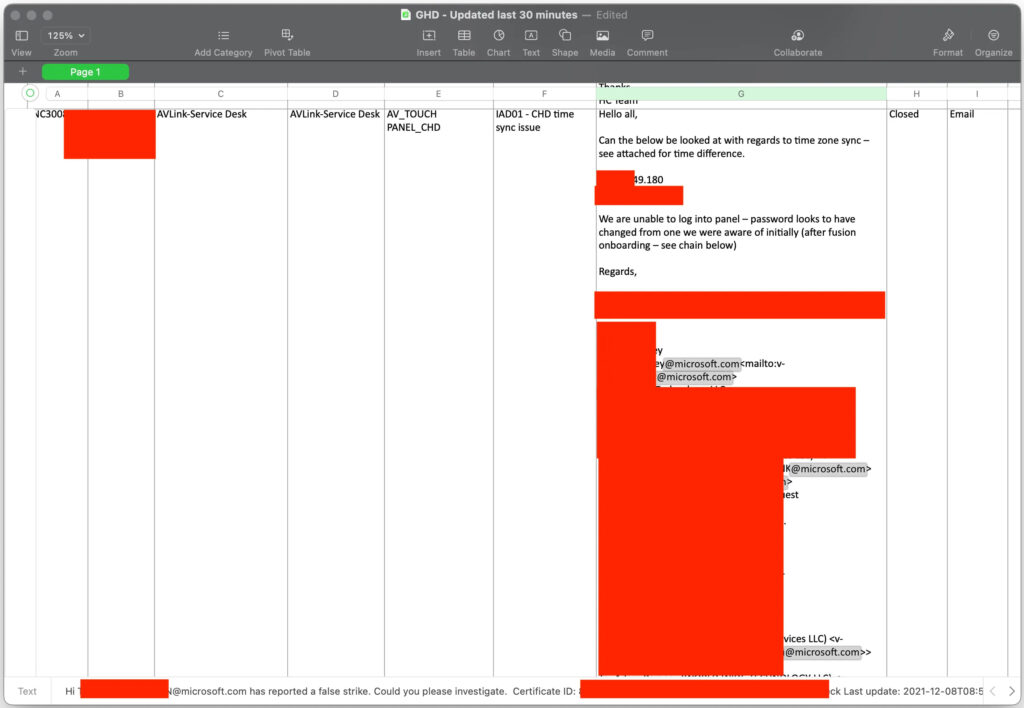
Microsoft’s ServiceNow platform manages various internal functions, including HR processes, employee onboarding, and support ticket handling. In this case, the compromised credential provided a gateway to the ServiceNow system, circumventing Microsoft’s Single Sign-On (SSO) requirement due to a legacy login option left active, likely for third-party access. Once logged in, Moblig explored ServiceNow’s REST API documentation and successfully retrieved data from specific endpoints.
Through these, the researcher accessed:
- Over 250,000 Microsoft employee email addresses alongside detailed personal information.
- Sensitive support ticket attachments containing onboarding details, internal support communications, and incident reports.
medium.com | @moblig
Moblig reported these findings to Microsoft’s Security Response Center (MSRC) on September 22, 2024. After investigating the vulnerability, Microsoft confirmed that a fix was implemented by October 16, 2024. However, Moblig noted that Microsoft did not offer any monetary bounty, even though the disclosure enabled a significant security enhancement.
Microsoft, like many large enterprises, relies on an internal management and detection response system, but the use of personal devices by employees remains a notable security gap as highlighted in this report.
Although Moblig acted responsibly in this case, reporting their findings to Microsoft, it wouldn’t be implausible to suggest that others before him didn’t act in the same manner, especially considering the relatively simple process involved in discovering the exposed instance.







Leave a Reply