
Security researchers from WatchTowr Labs accidentally took over the defunct domain of the WHOIS server for the .MOBI top-level domain (TLD), unveiling a major vulnerability in internet infrastructure. With just $20, the team not only achieved remote code execution (RCE) but also undermined the TLS/SSL certificate validation process for the entire .MOBI domain, effectively gaining the ability to impersonate any .mobi website.
Discovery and exploitation
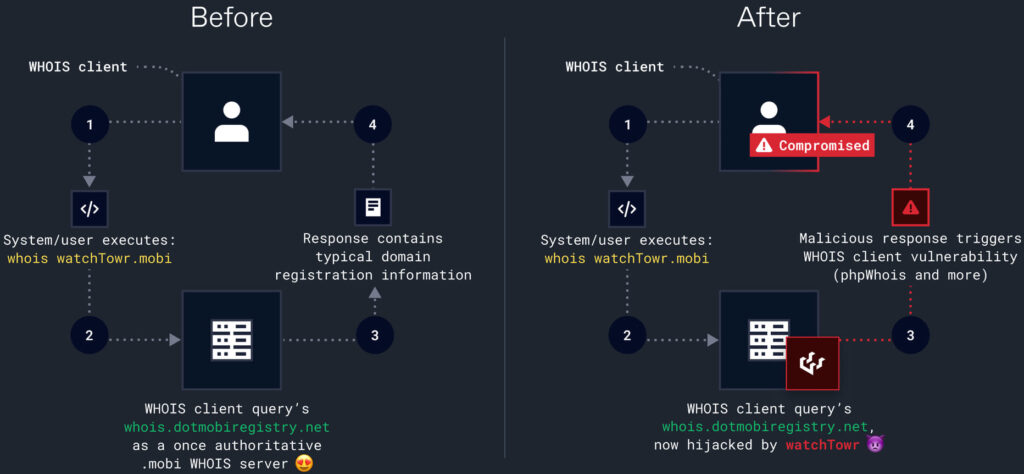
The discovery unfolded in late August 2024 during a research project aimed at testing vulnerabilities in WHOIS client parsing. While working at the Black Hat security conference, the WatchTowr Labs team noticed that the domain for the old .MOBI WHOIS server, whois.dotmobiregistry.net, had been left to expire. This legacy server had been replaced by whois.nic.mobi several years prior, but many systems still referenced the outdated address.
Realizing the potential implications, the researchers quickly purchased the expired domain. After setting up a WHOIS server under the acquired domain, they observed a massive influx of queries, with over 135,000 unique systems contacting the server and 2.5 million queries logged by early September 2024.
These queries came from various sources, including:
- Government and military entities (.GOV and .MIL domains).
- Cybersecurity companies like VirusTotal and URLScan.
- Certificate Authorities (CAs) responsible for issuing SSL/TLS certificates, including GlobalSign.
The most alarming discovery came when the team found that several Certificate Authorities were using their hijacked WHOIS server to verify domain ownership. By providing fake email addresses in WHOIS responses, the researchers could intercept domain verification emails for high-profile sites like microsoft.mobi and google.mobi, potentially enabling them to issue fraudulent TLS/SSL certificates.
Impact on internet security
The .MOBI TLD, launched in 2005, was designed for mobile-optimized websites. Although its use has declined in recent years, the TLD still supports various businesses, organizations, and government entities worldwide. By exploiting the expired WHOIS domain, the WatchTowr Labs team highlighted the risks posed by outdated infrastructure and poor maintenance practices.
The most significant threat discovered was the ability to subvert the Certificate Authority (CA) process. TLS/SSL certificates are crucial for securing internet communications, as they ensure that websites and services are authentic. By hijacking the WHOIS process and redirecting email validation to their own server, the researchers could have obtained valid certificates for any .mobi domain. This would allow attackers to launch man-in-the-middle (MITM) attacks, intercept encrypted traffic, or impersonate legitimate websites.
Measures and recommendations
Upon realizing the severity of their findings, the WatchTowr Labs team worked with the UK’s National Cyber Security Centre (NCSC) and the Shadowserver Foundation to mitigate the threat. The dotmobiregistry.net domain was redirected to a sinkhole operated by Shadowserver, which now proxies legitimate WHOIS responses for .mobi domains.
In response to this incident, WatchTowr Labs has issued the following recommendations:
- Organizations should ensure that their WHOIS clients are referencing the correct authoritative servers, especially for outdated TLDs.
- Administrators should regularly audit and renew expired domains, particularly those tied to critical infrastructure like WHOIS or DNS.
- Certificate Authorities should adopt stronger methods for domain verification, such as DNS-based verification, to reduce reliance on WHOIS data.






Leave a Reply