
A phishing campaign targeting a Malwarebytes employee used a convincing fake data breach alert from 1Password in an attempt to steal vault credentials.
The phishing email was received on October 2, and while blocked before damage could occur, the campaign reveals a growing trend of using social engineering aimed at breaching password manager accounts.
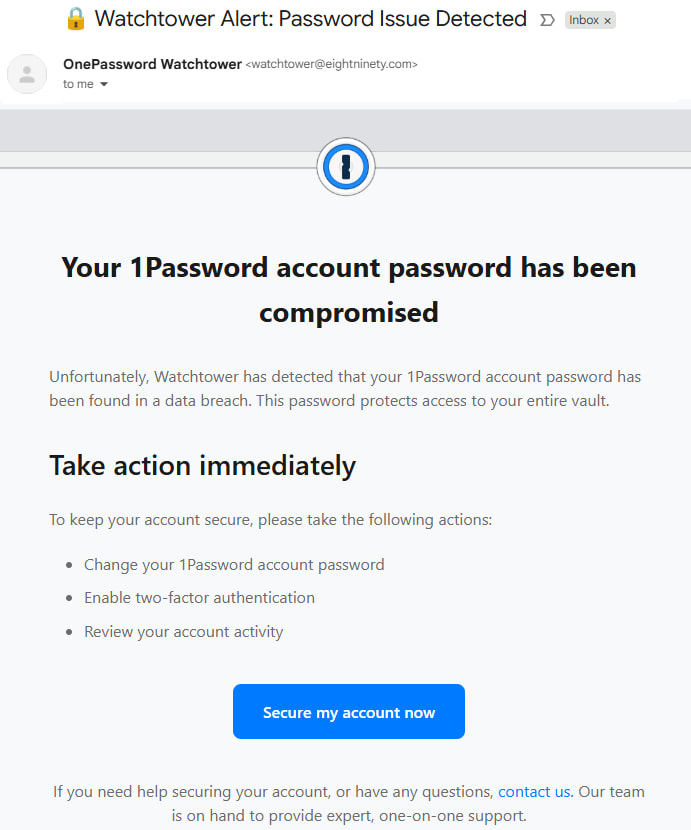
The attackers crafted a deceptive email that mimicked a breach notification from 1Password’s “Watchtower” system, urging the recipient to change their password and enable two-factor authentication. The email, which used the subject line “Your 1Password account has been compromised,” attempted to provoke urgency by implying that the vault password had been exposed in a recent data breach.
Malwarebytes
However, a closer inspection exposed several red flags:
- The sender's email address, watchtower@eightninety[.]com, does not belong to 1Password’s official domain (@1password.com).
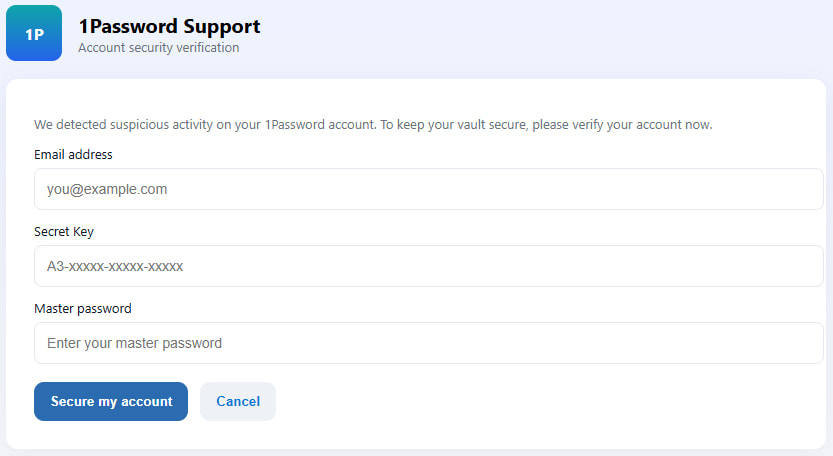
- The call-to-action button led to a malicious URL (onepass-word[.]com) via the Mandrillapp tracking service, an otherwise legitimate email infrastructure platform owned by Mailchimp.
- The site hosted a credential harvesting form closely mimicking the legitimate 1Password login interface.
1Password is one of the most widely used password managers globally, serving individuals, families, and enterprises. The application stores encrypted credentials and sensitive data in a vault, accessible only via a master password and optionally protected by multi-factor authentication. A compromise of a user’s 1Password vault could expose a vast trove of logins, secrets, and even digital identity artifacts.
The phishing domain, onepass-word[.]com, was quickly flagged as malicious by multiple security vendors and blocked by Malwarebytes. By October 3, users clicking the link were met with an error message from Mandrillapp indicating that the redirect had been disabled, minimizing further exposure. However, early victims who submitted their credentials to the phishing form may have had their entire password vaults compromised. Also, it’s very likely that the threat actors will reboot the campaign on a different domain, so vigilance is advised.
Malwarebytes
Malwarebytes noted that Mandrillapp’s involvement was incidental. The service is often used to send legitimate transactional emails, but it does not permit redirection to known phishing sites. The inclusion of legitimate-looking redirects, such as one leading to support.1password.com, further added to the email’s perceived authenticity, tricking even wary users.
This phishing attempt follows a similar campaign reported by Hoax-Slayer on September 25, 2025, suggesting a sustained effort by threat actors to exploit user trust in password managers. The repeated targeting of 1Password users could indicate either a broader campaign or a recycled phishing kit currently in circulation.







Leave a Reply