
Google Threat Intelligence Group (GTIG), in collaboration with industry partners, has dismantled what it identifies as one of the world’s largest residential proxy networks, IPIDEA.
The action targeted the infrastructure behind a sprawling ecosystem of proxy and VPN services that covertly turned millions of consumer devices into exit nodes for malicious activity.
The takedown involved legal action against control domains, technical coordination with platform providers and cybersecurity firms, and enforcement of Google Play protections. GTIG’s efforts degraded IPIDEA’s proxy operations at scale, disrupting a covert infrastructure that had been exploited by over 550 threat actors in a single week, ranging from cybercriminals to state-backed espionage groups.
IPIDEA operated a suite of proxy and VPN brands like Galleon VPN, Radish VPN, Door VPN, and Aman VPN, that offered what appeared to be legitimate services. In reality, many of these brands, including 360 Proxy, Luna Proxy, IP2World, and Cherry Proxy, secretly enrolled user devices into a massive proxy network via trojanized apps or embedded SDKs. These SDKs were integrated into hundreds of apps across Android, Windows, iOS, and WebOS platforms, often without user awareness or consent.
GTIG’s investigation revealed that these software development kits, marketed under names such as PacketSDK, EarnSDK, HexSDK, and CastarSDK, transformed everyday devices into proxy exit nodes. Once infected, a user’s device could be silently used to route traffic for attackers, enabling activities such as password spraying, infrastructure access, and exploitation of SaaS platforms. Devices in the United States, Canada, and Europe were especially sought after, due to the relative trustworthiness of IP addresses in these regions.
The broader danger lies not only in facilitating threat actor obfuscation but in the risk to individuals whose devices are compromised. When a device becomes an exit node, it may inadvertently host malicious traffic, exposing the owner to reputational harm, ISP blacklisting, or network intrusion. GTIG's analysis showed that some proxy SDKs didn't just route traffic through a device, they also received inbound traffic, opening pathways for lateral movement and further compromise within home networks.
IPIDEA’s proxy infrastructure was structured around a two-tier command-and-control (C2) model. Tier One servers directed infected devices to a rotating set of Tier Two nodes, which issued proxy instructions and routed payloads. GTIG identified approximately 7,400 Tier Two servers globally, suggesting a flexible and demand-driven backend architecture. Despite the use of multiple brands and domains, forensic analysis showed the same underlying infrastructure was reused across SDKs and proxy services, confirming centralized control.
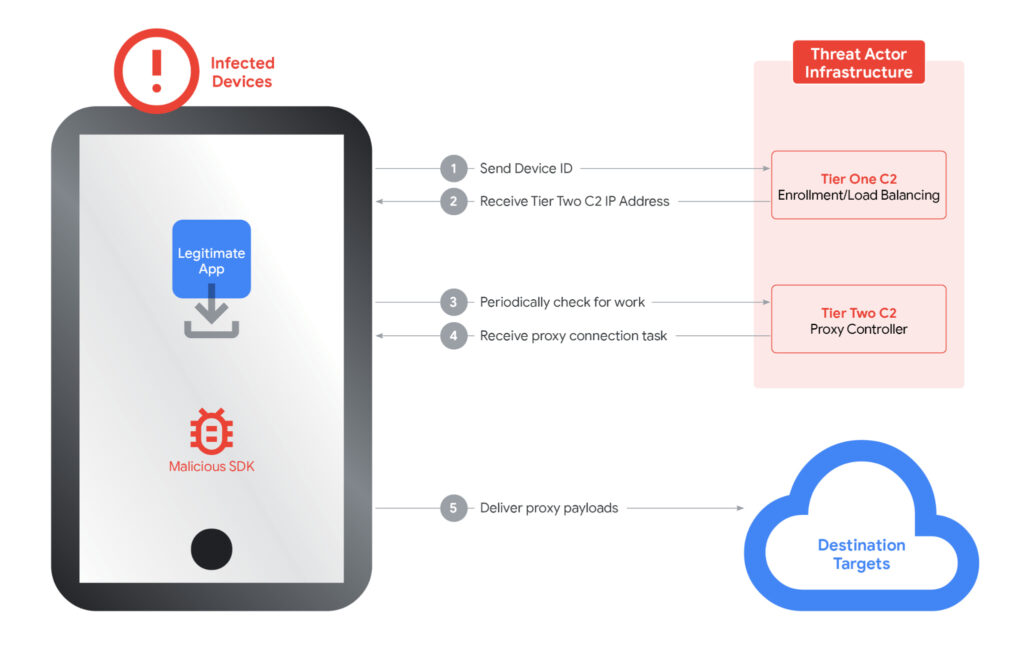
GTIG identified over 600 Android applications and more than 3,000 Windows binaries communicating with IPIDEA’s control infrastructure. Many of these were repackaged utilities or benign-looking apps that offered superficial functionality while silently enrolling the device into the proxy network. Others mimicked trusted system tools like OneDrive Sync or Windows Update to evade detection.
GTIG also linked the SDK infrastructure to previously identified malware campaigns including BadBox2.0, Aisuru, and Kimwolf, suggesting that residential proxy enrollment was used to support both infection and command infrastructure. State-sponsored actors from China, North Korea, Iran, and Russia were observed leveraging IPIDEA exit nodes for covert operations, highlighting the network’s strategic value.
The disrupted services include not only the SDKs and proxy brands but also associated marketing and distribution domains. Google also collaborated with firms like Spur, Cloudflare, and Lumen’s Black Lotus Labs to map and block IPIDEA’s DNS and C2 infrastructure. Enforcement actions targeted domains tied to SDK distribution, including packetsdk[.]io, castarsdk[.]com, and earnsdk[.]io.
Consumers are urged to remain vigilant. Applications that promise payment for sharing “unused bandwidth” or offer “free” VPN services may be enrolling devices into proxy networks without consent. These apps can introduce vulnerabilities, degrade performance, and expose households to legal or cybersecurity consequences. Users should stick to trusted app sources, regularly audit installed apps and permissions, and confirm that their devices are Play Protect certified.






Leave a Reply