
Malicious Chrome extensions exploit the surge in popularity of generative AI tools to deploy spyware that steals browsing and Gmail data.
LayerX uncovered at least 30 separate extensions that funnel user data to attacker-controlled infrastructure through remotely loaded iframes.
The researchers discovered a set of extensions using identical architecture, permissions, and infrastructure, despite differing names and branding. These extensions, some of which were even marked as “Featured” by the Chrome Web Store, collectively impacted over 260,000 users. The threat actors behind the operation implemented an evasive tactic known as extension spraying, allowing them to maintain persistent distribution across multiple listings and identities.
Rather than functioning as genuine AI tools, the extensions act as front ends for remote interfaces hosted on the tapnetic[.]pro domain. Once installed, they inject full-screen iframes into users’ browsers, effectively placing a third-party-controlled interface atop every visited site. Because the logic and UI are served remotely, attackers can modify behavior in real time without pushing updates, completely bypassing Chrome Web Store review mechanisms.
Each malicious extension communicates with a unique subdomain under tapnetic[.]pro, themed to resemble the impersonated AI assistant. Although the base domain hosts a generic marketing site, researchers concluded that it serves as a cover for malicious backend activity. All subdomains display consistent behavior and request structure, signaling a single, coordinated backend system.
This iframe-centric design grants attackers broad capabilities:
- Full access to readable webpage content via Mozilla’s Readability library
- Voice recognition using the Web Speech API
- Real-time UI updates and logic injection from remote servers
- Stealth data extraction, including from internal and authenticated pages
LayerX
Gmail surveillance
A particularly invasive subset of 15 extensions explicitly targeted Gmail users. These tools injected scripts directly into mail.google.com using document_start triggers and manipulated the DOM to extract visible message content. The harvested email data, including entire threads, drafts, and reply text, was transmitted to the attacker's infrastructure when users interacted with features like AI summaries or auto-responses.
To remain persistent, the Gmail modules relied on DOM MutationObservers and polling loops to survive interface changes. The extensions mimicked legitimate productivity features while quietly siphoning sensitive communication content to third-party servers.
LayerX observed active efforts to evade detection and takedown. One extension, “Gemini AI Sidebar,” was removed from the Chrome Web Store on February 6, 2025. Just two weeks later, a clone was uploaded with a new ID, identical code, and unchanged backend links.
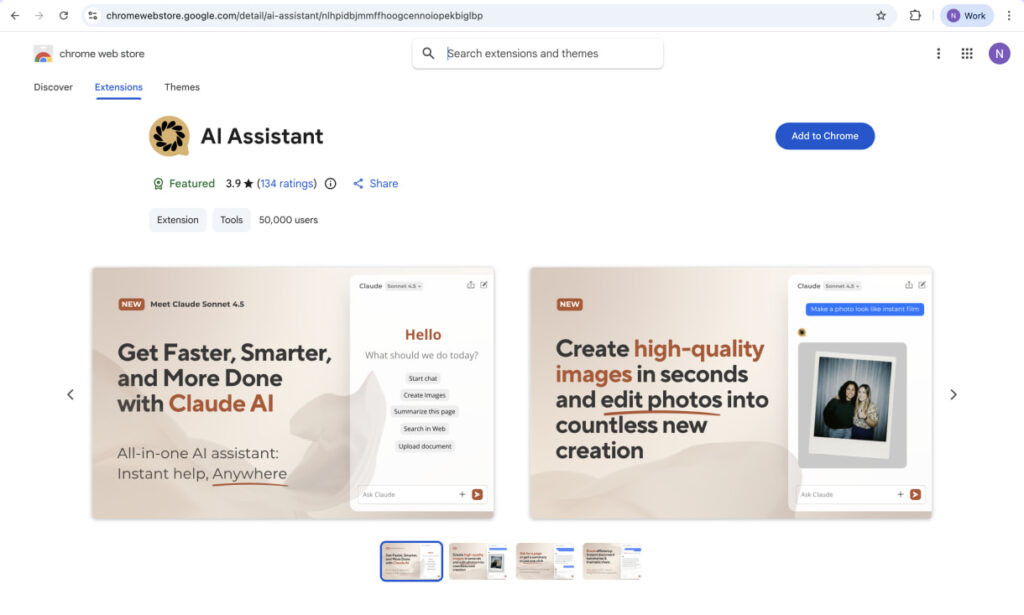
The most downloaded of the malicious extensions used in the campaign are:
- AI Assistant – (nlhpidbjmmffhoogcennoiopekbiglbp) – 50,000 installs
- Gemini AI Sidebar – (fppbiomdkfbhgjjdmojlogeceejinadg) – 80,000 installs
- AI Sidebar (re-upload) – (gghdfkafnhfpaooiolhncejnlgglhkhe) – 50,000 installs
- ChatGPT Sidebar – (llojfncgbabajmdglnkbhmiebiinohek) – 10,000 installs
- Google Gemini – (fdlagfnfaheppaigholhoojabfaapnhb) – 7,000 installs
- ChatGBT – (pgfibniplgcnccdnkhblpmmlfodijppg) – 1,000 installs
- Ask Gemini – (gnaekhndaddbimfllbgmecjijbbfpabc) – 1,000 installs
- DeepSeek Chat – (gohgeedemmaohocbaccllpkabadoogpl) – 1,000 installs
- ChatGPT Translate – (acaeafediijmccnjlokgcdiojiljfpbe) – 30,000 installs
- AI GPT – (kblengdlefjpjkekanpoidgoghdngdgl) – 20,000 installs
- ChatGPT Translation – (idhknpoceajhnjokpnbicildeoligdgh) – 1,000 installs
- Chat GPT for Gmail – (fpmkabpaklbhbhegegapfkenkmpipick) – 1,000 installs
Users who have installed any of the 30 extensions listed in LayerX’s report should remove them immediately, perform password resets, and consider their Gmail communications fully compromised.







Leave a Reply