
A shady Chinese VPN platform serving devices in Russia, China, Myanmar, Iran, and Venezuela is using a global proxying network to bypass heavy internet censorship or international sanctions.
The probe, powered by Silent Push’s investigation and residential proxy datasets, revealed a sprawling infrastructure behind a low-quality VPN, dubbed LVCHA VPN, that appears to bypass regional firewalls and obscure its origins using residential IPs.
The discovery stemmed from a deep-dive into traffic associated with IP address 205.198.91[.]155, which Silent Push’s global observation network flagged for its unusual geographic distribution. The Traffic Origin telemetry revealed traffic exclusively from five authoritarian states, an anomaly suggesting the platform might be facilitating sanctioned activity or surveillance evasion. Additional DNS data linked this IP address to the domain lvcha[.]in, a Chinese-language website that offers a downloadable Android VPN APK outside the Google Play Store.
The LVCHA VPN site misleadingly claims to have passed Google's security checks, though its distribution method, direct sideloading, actually bypasses standard Android security protocols. The site provides no iOS version. The domain, registered in March 2024 through NameSilo, exclusively serves Mandarin content and promotes itself as a free VPN.
Silent Push, a cybersecurity intelligence firm known for uncovering hidden infrastructure using passive DNS and web metadata analysis, contextualized the platform’s ecosystem using its Web Search tool. The analysts identified nearly 50 domains cloned from lvcha[.]in, all of which share key technical indicators, including shared JavaScript hashes (ssdeep), Telegram handles, and favicon MD5 hashes.
Among the identified domains are variants like lcapp[.]shop, lcvpn[.]top, and lvchaapp[.]vip, suggesting a strategy of rapid domain rotation to evade detection or censorship. This approach is often observed in operations seeking to skirt China's “Great Firewall” or similar filtering systems deployed in Russia, Iran, Myanmar, and Venezuela.
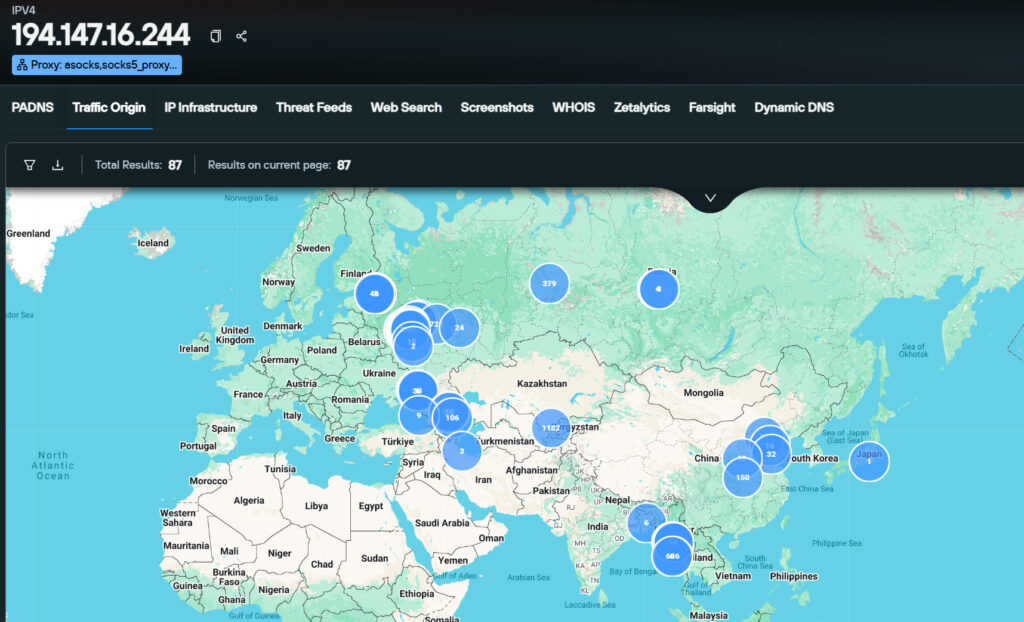
The backend infrastructure points to multiple IP addresses across different networks. IP 205.198.91[.]136, used by Asocks Proxies (asocks[.]com), shows traffic not just in the original five countries but also in Russian-occupied eastern Ukraine. Another IP, 194.147.16[.]244, part of UK-based AS48266, hosts identical VPN content and reflects traffic from a broader geopolitical spread, including Russia, Bangladesh, Kazakhstan, Georgia, Japan, and areas near the Ukrainian border.
Silent Push
LVCHA’s widespread geographic footprint, particularly its heavy usage in Moscow and border regions, suggests that it may be leveraged for both domestic censorship circumvention and possibly covert operations. While the true operators remain unknown, the use of residential proxies, clone infrastructure, and Telegram promotion aligns with previous tactics seen in state-aligned or gray-market digital operations.







Leave a Reply