
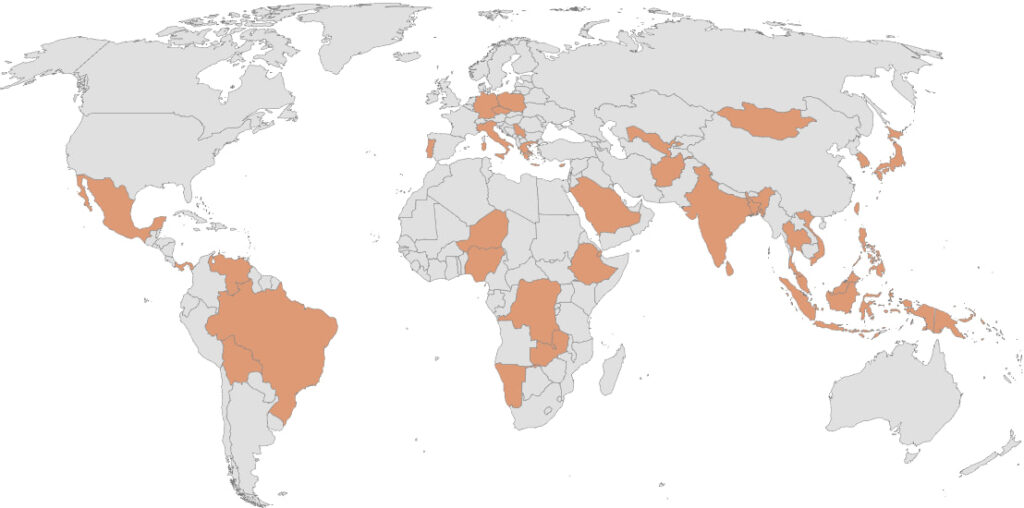
A newly identified cyber-espionage group tracked as TGR-STA-1030, dubbed the “Shadow Campaigns,” has breached at least 70 high-value government and critical infrastructure entities across 37 countries.
The group has been active since at least early 2024, ramping up operations through 2025 with an aggressive mix of phishing campaigns, exploitation of known vulnerabilities, and stealthy persistence tools, including a custom Linux rootkit.
Unit 42 began tracking TGR-STA-1030 in early 2025 during investigations into phishing attacks against European governments. The group, assessed with high confidence to be state-aligned and operating out of Asia, has since expanded its operations to nearly every region of the globe. Infrastructure analysis shows consistent use of regional language settings, operational hours aligned with GMT+8, and upstream connections tracing back to Autonomous System 9808, an ISP located in the group's home region.
The espionage activity, now collectively known as the Shadow Campaigns, has targeted ministries of finance, foreign affairs, trade, and interior, alongside national law enforcement bodies, parliaments, and even a major Taiwanese power equipment supplier. Victims include countries across Europe, the Americas, Asia-Pacific, and Africa.
Unit 42
Shadow Campaigns tactics and tooling
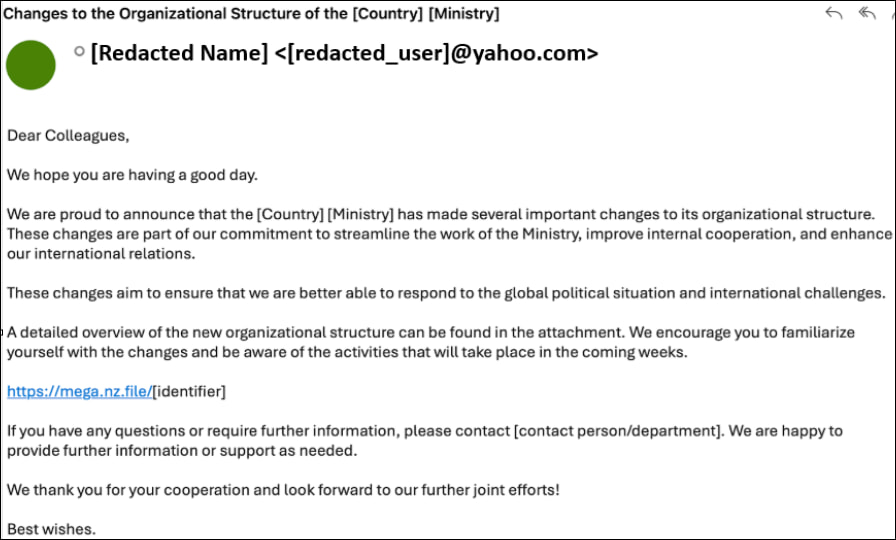
The group employs a multi-pronged approach combining phishing, n-day exploit deployment, and custom malware. One of its earliest operations involved phishing emails mimicking government restructuring notices, linking to malicious ZIP files hosted on mega[.]nz. These files delivered a staged malware loader, identified as Diaoyu Loader, which uses environmental checks to evade sandbox detection. A key feature is the requirement for a dummy file (pic1.png) to be present, acting as an integrity gate before malware execution proceeds.
Unit 42
Once activated, the loader checks for select antivirus products (Kaspersky, Avira, Bitdefender, Sentinel One, Symantec), downloads additional payloads from GitHub, and eventually deploys Cobalt Strike, a commercially available C2 framework frequently used by threat actors.
Over time, TGR-STA-1030 has diversified its arsenal, favoring VShell, a Go-based C2 framework, and tools like Havoc, Sliver, and SparkRAT for lateral movement. For persistence and stealth, the group frequently deploys web shells, including Behinder, Neo-reGeorg, and Godzilla, often obfuscated using open-source projects like Tas9er.
A standout discovery is the group’s development of a custom eBPF-based Linux rootkit, ShadowGuard, capable of hiding processes, directories, and network activity at the kernel level. With capabilities such as syscall interception, PID allow-listing, and kernel-space execution, ShadowGuard is designed for deep stealth and resilience, and is so far unique to this group.
Reconnaissance activity surged in late 2025, with scanning campaigns targeting government infrastructure in 155 countries between November and December alone. Unlike typical wide-net scans, TGR-STA-1030's activity is highly curated, focusing on high-value ministries and public institutions.
Among its confirmed compromises are:
- Brazil: Ministry of Mines and Energy, aligning with US efforts to diversify rare earth mineral sourcing
- Taiwan: Power equipment supplier, indicating interest in critical infrastructure
- Czechia: Post-Dalai Lama meeting, the group targeted the President’s site and multiple ministries
- Mexico: Two ministries compromised within 24 hours of trade policy announcements
- Indonesia: Law enforcement and airport-linked systems accessed amid mining and aviation developments
- Zambia & DRC: Ministries compromised following environmental incidents involving Asian mining firms
Unit 42 analysts note a pattern of economic intelligence collection, with timing often aligned with international summits, resource negotiations, or diplomatic events.
One of the most advanced tools the attackers used in these campaigns is ShadowGuard, a stealthy kernel rootkit built on eBPF (Extended Berkeley Packet Filter) technology. Designed to remain invisible to user-space monitoring tools, ShadowGuard can hide up to 32 processes, directories named swsecret, and provides an allow-listing system to manage visibility.
By operating entirely in kernel space without appearing as a module, the rootkit significantly complicates detection even by advanced endpoint monitoring tools.
Defenders are advised to apply security updates for known flaws, monitor for anomalous outbound connections, and harden SSH and RDP endpoints. A complete list of indicators of compromise is provided on the Unit 42 report to help defenders hunt for these attacks.







Leave a Reply