
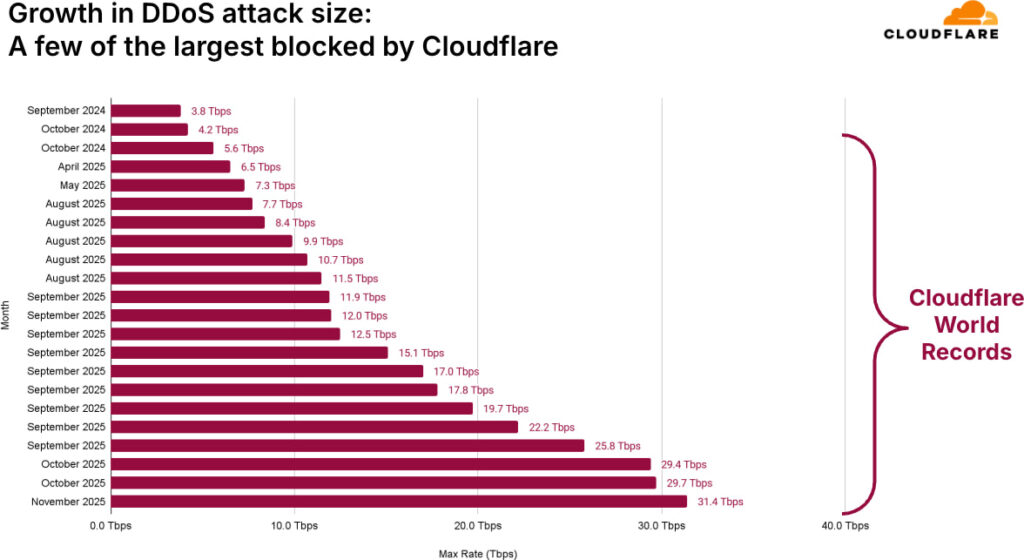
Cloudflare successfully mitigated a new record-setting Distributed Denial-of-Service (DDoS) attack that peaked at 31.4 terabits per second (Tbps), the largest ever disclosed publicly.
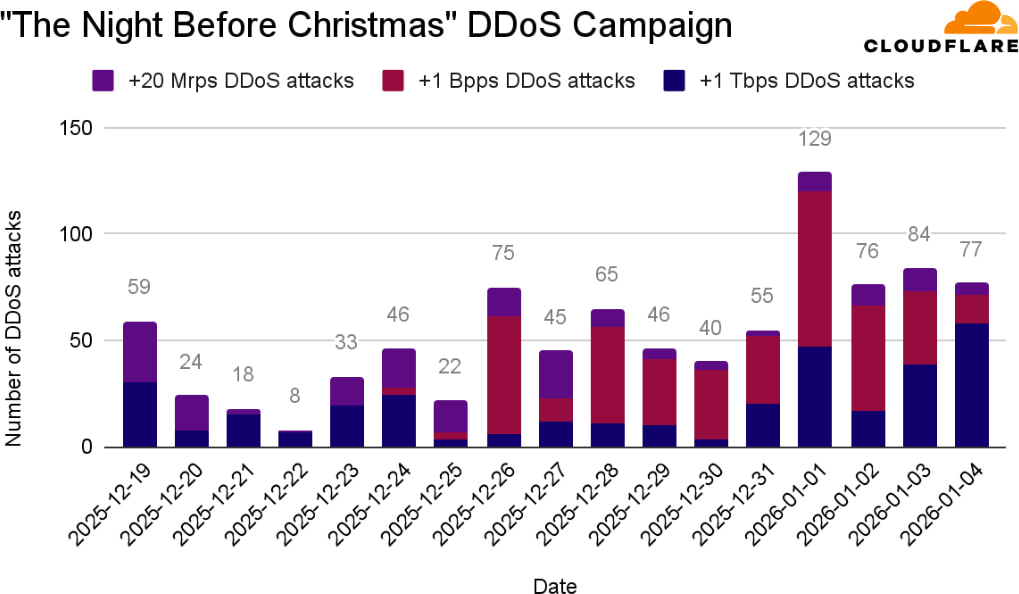
The staggering 31.4 Tbps attack was part of a broader surge of hyper-volumetric DDoS activity, most notably orchestrated by the Aisuru-Kimwolf botnet, a rapidly growing botnet made up predominantly of infected Android TV devices. The botnet also launched the so-called “Night Before Christmas” campaign in December 2025, flooding Cloudflare’s network and its customers with hyper-volumetric HTTP DDoS attacks reaching 205 million requests per second (Mrps) and 24 Tbps in traffic, another near-record-breaking figure.
According to Cloudflare’s Q4 2025 DDoS Threat Report, 2025 saw a 121% year-over-year increase in the volume of DDoS attacks, totaling 47.1 million incidents, more than double the count from 2024.
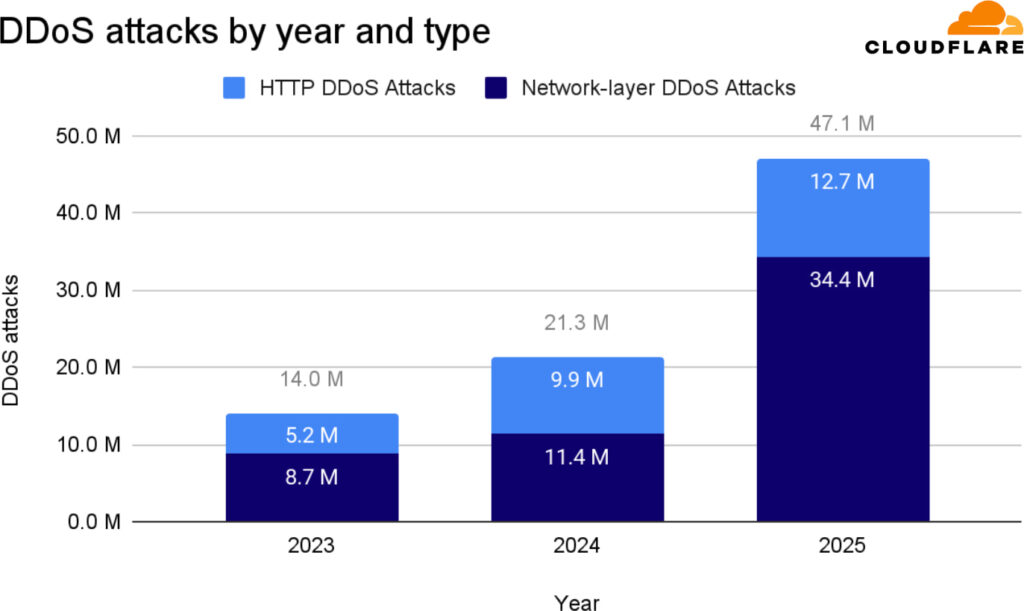
Network-layer DDoS attacks grew most sharply, tripling over the year to reach 34.4 million, while HTTP DDoS attacks, although fewer in number, surged in size, particularly in the final quarter. Cloudflare mitigated an average of 5,376 attacks per hour in 2025, automatically filtering out malicious traffic at a rate that defies traditional detection-and-response methods.
The 31.4 Tbps attack, which lasted just 35 seconds, represents a 700% increase in peak attack size compared to late 2024 figures.
At the center of many of these assaults is the Aisuru-Kimwolf botnet, also responsible for a 29.7 Tbps attack in October 2025. The botnet appears to control 1 to 4 million devices globally, primarily Android-based smart TVs. These compromised systems have proven effective at overwhelming legacy cloud defenses and even destabilizing national-level infrastructure.
The December 2025 campaign saw 902 distinct DDoS attacks, with individual attack bursts averaging 3 billion packets per second (Bpps), 4 Tbps, and 54 Mrps. The peak values, 9 Bpps, 24 Tbps, and 205 Mrps, signal a dramatic shift in attacker capabilities, leveraging botnets built from low-cost consumer hardware to deliver enterprise-grade impact.
Targeted industries
Cloudflare reports that Telecommunications providers, ISPs, and cloud service carriers were the primary targets in 2025, followed by the gaming and generative AI sectors. The Information Technology & Services industry, previously the most targeted, was surpassed, underlining the shifting priorities of attackers toward high-impact, high-visibility sectors.
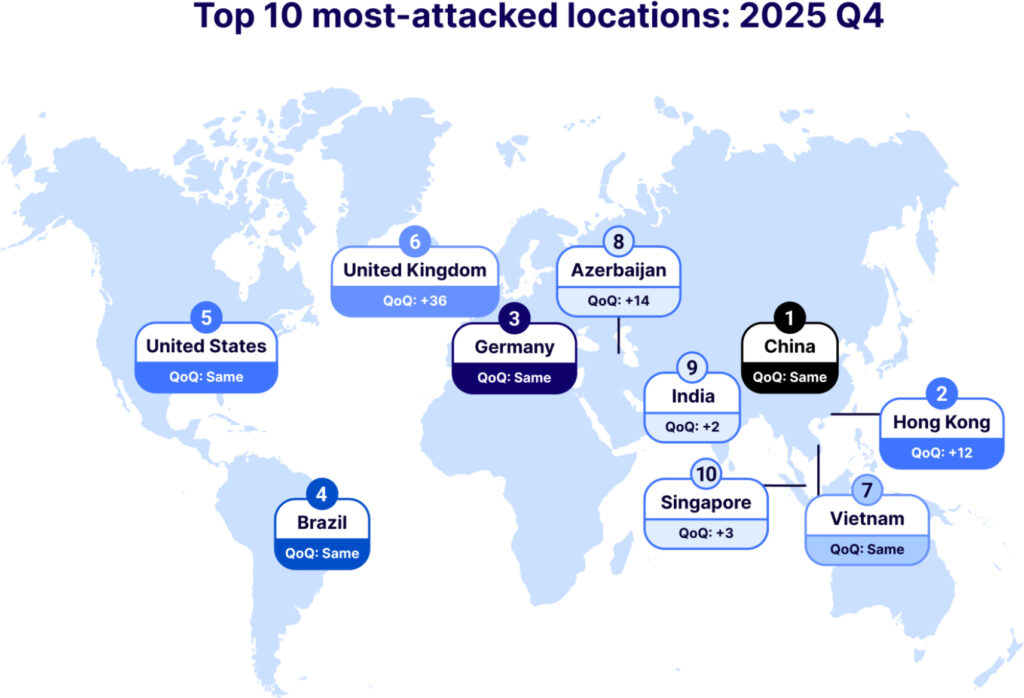
Geographically, the United Kingdom saw the most dramatic change, leaping 36 places to become the sixth most-attacked country. Hong Kong also rose sharply, now ranked second. Meanwhile, Bangladesh emerged as the top source of DDoS traffic in Q4, displacing Indonesia after a year-long reign. Argentina notably jumped 20 positions to become the fourth-largest source.
The primary attack origins trace back to cloud providers and telecom networks, with DigitalOcean, Microsoft, Tencent, and Oracle listed as the top source networks. Attackers appear to be leveraging virtual machines from commercial cloud platforms to launch scalable, low-cost DDoS campaigns.







Leave a Reply