
A dual-stage malware campaign leveraging a previously undiscovered loader, RenEngine, has infected over 400,000 systems globally, with more than 5,000 new infections daily.
Active since at least April 2025, the operation uses cracked versions of popular AAA games as a vector for stealthy information stealers.
The campaign was uncovered by researchers at Cyderes who identified a novel loader embedded in modified Ren'Py-based game launchers. These launchers are packaged with pirated copies of games such as Far Cry, FIFA, Need for Speed, and Assassin’s Creed. Users who download these games from piracy websites unknowingly initiate the first stage of the infection, which quietly launches the RenEngine Loader.
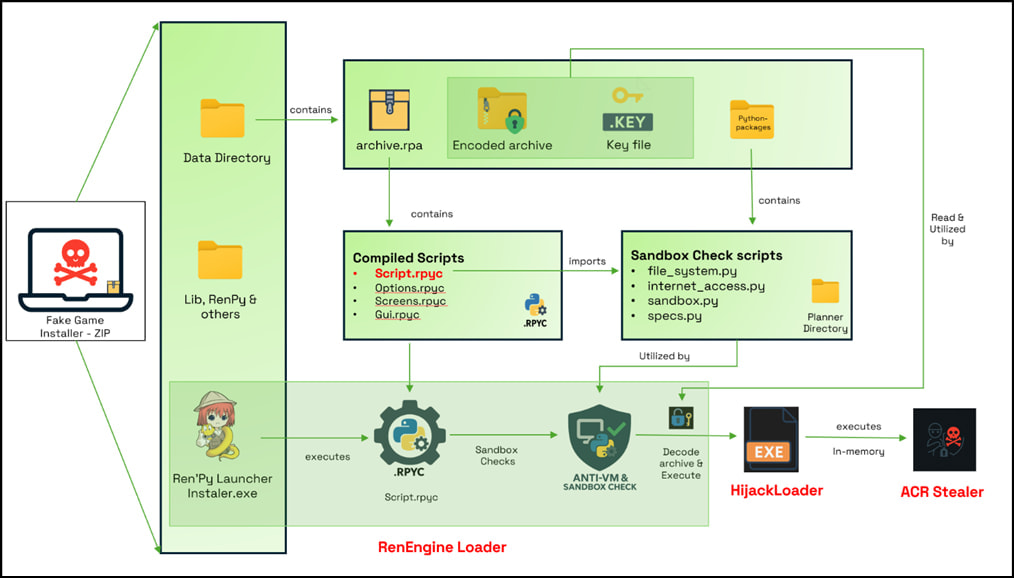
The loader abuses Ren’Py, a legitimate game development engine, to deploy Python-based malicious scripts disguised within game archives. It performs sandbox checks before deploying a second-stage payload, HijackLoader, which is heavily modular and capable of process hollowing, DLL side-loading, call stack spoofing, and process doppelgänging.
Stage 1 – RenEngine Loader is executed through a legitimate-looking launcher (Instaler.exe) that decompresses and runs a compiled Python script (script.rpyc) from an embedded .rpa archive. The loader decodes a configuration file using Base64 and XOR, checks for virtual environments using a multi-factor scoring system (evaluating RAM, CPU cores, disk space, BIOS serials, registry keys, and known virtualization artifacts), and then decrypts and executes the next stage.
If the system passes these checks, RenEngine decodes an XOR-encrypted ZIP archive containing a signed executable (W8CPbGQI.exe) that is used to side-load malicious DLLs — an evasion technique that allows the malware to execute under the guise of trusted processes.
Stage 2 – HijackLoader then executes, using side-loaded DLLs like VSDebugScriptAgent170.dll and d3dx9_43.dll to perform module stomping and dynamic code injection. Configuration data is hidden in an encrypted file (Froodjurain.wkk) using a custom IDAT structure with magic headers and XOR encryption. This allows HijackLoader to load an array of 38 modules, providing a wide range of capabilities, including:
- VM and sandbox detection (ANTIVM, ANTIVMGPU, ANTIVMHYPERVISORNAMES)
- Credential theft and browser data exfiltration
- UAC bypass and persistence mechanisms
- Reverse shell creation
- Security product detection and interference
- Flexible injection and payload loading routines
The final stage of the attack involves deploying the ACR Stealer, a widely used infostealer that extracts browser passwords, cookies, session tokens, cryptocurrency wallets, clipboard contents, and system information. The stolen data is exfiltrated to a command-and-control server located at 78.40.193.126, with a campaign ID embedded for tracking.
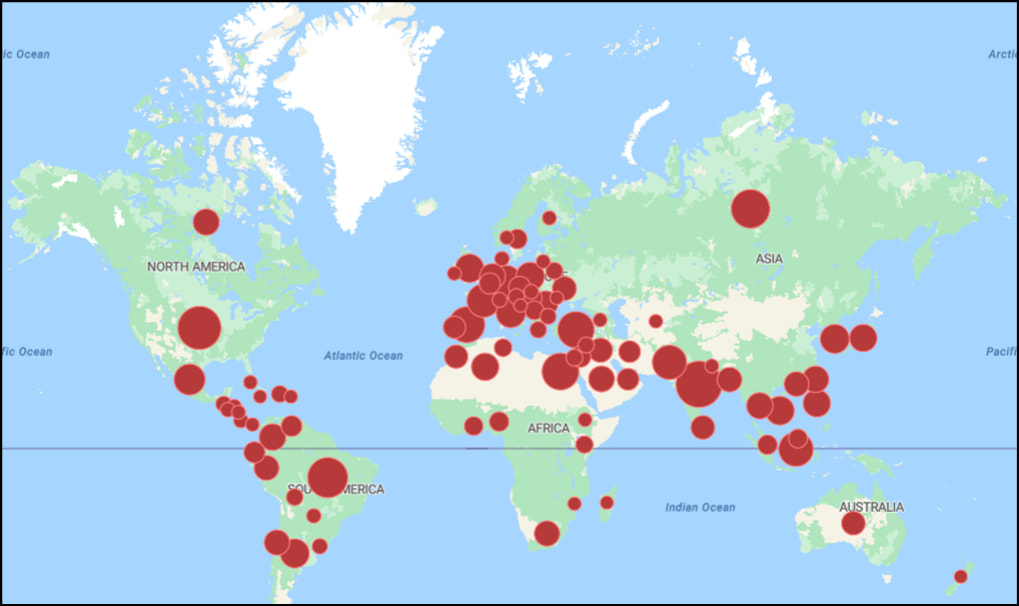
Global campaign impact
Since October 2025, the malware has incorporated telemetry tracking, allowing operators to monitor infections in near real time. The malware sends analytical pings to a hidden server whenever the RenEngine Loader runs. These telemetry logs show a steady infection curve, with peak activity in December 2025.
Top affected countries include:
- India – 38,016 victims
- United States – 31,317
- Brazil – 25,220
- Russia, Egypt, Turkey, and France follow closely
The malware distribution relies entirely on social engineering, capitalizing on user trust in piracy and modding communities. Victims typically download the infected installers from known sites like dodi-repacks[.]site, which redirects to MediaFire to serve the malicious ZIP files.
To mitigate the risk, users should avoid downloading pirated game installers, which are often bundled with malware, and stick to legal software distribution channels for safety.







Leave a Reply