
A newly disclosed vulnerability in Chrome allows browser extensions to extract the full URL of any tab, even without explicit permissions, by exploiting subtle timing differences in the declarativeNetRequest API.
The issue was reported by security researcher Luan Herrera (@lbherrera_) on January 28, 2026, via the Chromium bug tracker. Herrera demonstrated that an extension with only the declarativeNetRequest (DNR) permission can infer sensitive data from the address bar via a side-channel attack that exploits timing differences in response times between blocked and allowed requests. The vulnerability affects multiple Chrome versions, including the latest stable release and all major development channels.
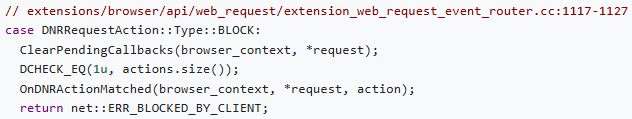
The technique works by dynamically injecting URL-blocking rules via regular expressions and using chrome.tabs.reload() to retrigger navigation to a target tab. The extension then measures how long it takes for the page to complete loading, using chrome.tabs.onUpdated. Because blocked requests fail almost instantly (net::ERR_BLOCKED_BY_CLIENT), while allowed requests continue with network activity, the difference in response time (~10–30ms for blocked vs. ~50–100ms for allowed) serves as a timing oracle.
Chromium
This timing signal is sufficient for a malicious extension to perform a character-by-character binary search across the entire URL string, gradually reconstructing it without any need for traditional tabs or host permissions.
Herrera provided proof-of-concept code and a reproduction video demonstrating the attack in action. His testing confirmed that sensitive URLs, such as those containing OAuth authorization codes, session tokens, password reset links, and private search queries, can be silently exfiltrated without user interaction or UI indicators. Notably, URLs used by platforms like YouTube, Google Drive, Dropbox, and many OAuth-based services could be silently leaked.
The vulnerability exploits a feature introduced in Chromium revision 1539dcc828ee3, which enabled regex rule evaluation for dynamic blocking. However, Herrera notes that variations of the attack may be viable as far back as the initial rollout of the Dynamic Rules API in commit 1531023, suggesting a long-standing issue.
Flaw deemed unfixable
Despite acknowledging the risk, Chromium developers have labeled the issue “Infeasible” to fix and marked it as “Won't Fix”, citing architectural limitations. The Extension Platform team concluded there’s no practical way to eliminate the side channel without significantly altering the performance characteristics of the web request system.
Herrera, in response, argued that while a complete mitigation may be unrealistic, the permissions disclosure should be updated. He suggested that the Chrome Web Store listing for DNR-based extensions should inform users that the extension could effectively access browsing history, similar to what the tabs permission entails.
Chromium eventually made the issue public on February 2, 2026, per the researcher’s request.
For Chrome users, the best defense is to limit the number of installed extensions and use only add-ons from reputable publishers, as even minimal permissions can carry more power than expected. For sensitive workflows, use dedicated browser profiles or containers.







Leave a Reply