
An activist platform designed to track US immigration enforcement activity, StopICE.net, has come under fire after reports surfaced of a major data breach that allegedly compromised the personal information of over 100,000 users and handed it to federal authorities.
StopICE.net serves as a crowdsourced alert network to monitor ICE activities across the United States. Users can report suspected immigration enforcement activity, such as van sightings, license plates, and time-stamped locations, through the site or via text. With over half a million subscribers, the platform has become a significant tool for immigrant defense and rapid-response organizing, particularly in sanctuary cities and border states.
Initial reports, which circulated widely on Reddit and other social media platforms, suggested that the StopICE platform had been hacked, with sensitive user data, names, phone numbers, login credentials, and even GPS locations, allegedly sent to the FBI, ICE, and Homeland Security Investigations (HSI). User posts claim they received strange and threatening messages from the phone number associated with the StopICE alert system, adding to fears that the site had been compromised at a deep level.
The situation escalated after online rumors pointed to Sherman Martin Austin, the platform's developer, accusing him of negligence in handling the breach. Austin, a known anarchist, served prison time in 2002 under federal charges related to online activism. Some argue that Austin’s past legal issues and decision not to immediately inform users may have compounded the risk.
StopICE denies breach
In a lengthy statement released over the weekend, the StopICE team rejected claims that any personal user data was exposed or handed over to authorities. According to them, the platform does not collect names, addresses, or precise GPS coordinates from its users. Instead, it uses anonymized polar coordinate calculations based on ZIP codes to trigger location-based alerts.
The statement also attributes the attempted breach to a personal server allegedly tied to a Customs and Border Protection (CBP) agent in Southern California. The attackers reportedly tried to inject false alerts into the system but were unsuccessful, the platform says, due to countermeasures and quick isolation of the attack vector. The operators claim the attackers fell for “bait” in the form of fake data and API keys, enabling StopICE to trace their networks and even publish associated IP addresses and phone numbers.
StopICE further downplayed the scale of the incident, claiming the only exposure involved temporary file names after a backend management tool update modified security headers, an issue they say was minor and resolved swiftly.
Worries remain
While StopICE positions itself as a protected free speech initiative, watchdog groups have previously flagged the platform for low transparency scores, recent domain registration, and potential security weaknesses. This week’s events have intensified scrutiny, especially as reports of spoofed texts and potential unauthorized access continue to surface.
On Reddit, users described receiving cryptic or threatening text messages from what appeared to be the official StopICE number. Some suspected the messages were sent via spoofing, in which attackers fake the sender's number to appear legitimate, while others warned that such targeted messages implied that attackers had accessed actual subscriber phone numbers.
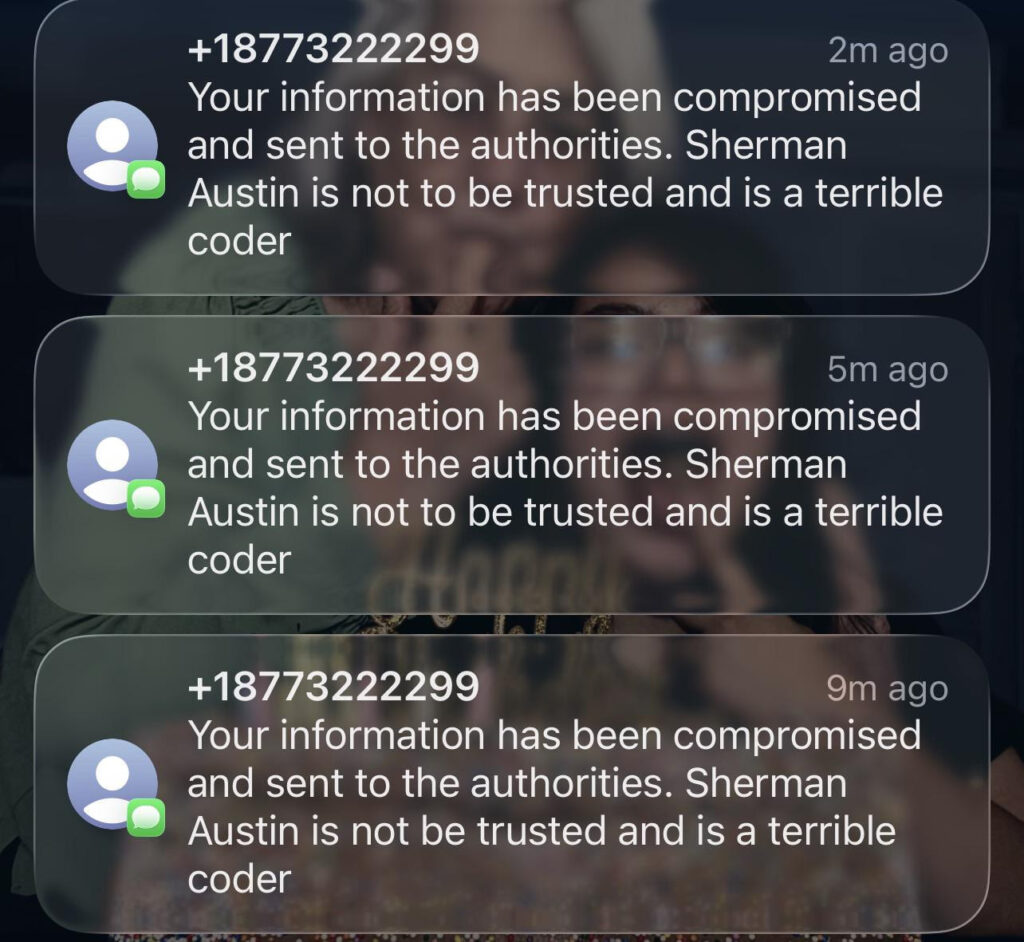
Commenters debated whether this confirmed a backend breach or was simply opportunistic trolling. Regardless, many users expressed feeling alarmed and exposed. Some also noted the site’s temporary outages during the incident, which StopICE attributes to sustained DDoS attacks, over 500 in a single day, by their count.
Adding to the confusion, screenshots and group chats began circulating that referenced groups like “datarepublican” sharing user lists, further fueling concerns that phone numbers tied to the platform were circulating.
Potentially exposed users are recommended to change any passwords associated with StopICE.net, avoid engaging with unsolicited messages, and use encrypted communication tools to share sensitive information.







Leave a Reply