
A malicious NPM package masquerading as a WhatsApp API library has been discovered exfiltrating users' messages, credentials, contacts, and media, all while delivering fully functional code.
The package, named lotusbail, had been available on the NPM registry for over six months, amassing more than 56,000 downloads before its true purpose came to light.
The discovery was made by Koi Security, whose researchers published a detailed technical report over the weekend, outlining the package's behavior. The threat actor behind lotusbail cloned the legitimate @whiskeysockets/baileys WhatsApp Web API library and inserted advanced malware designed to siphon off sensitive user data during normal operation.
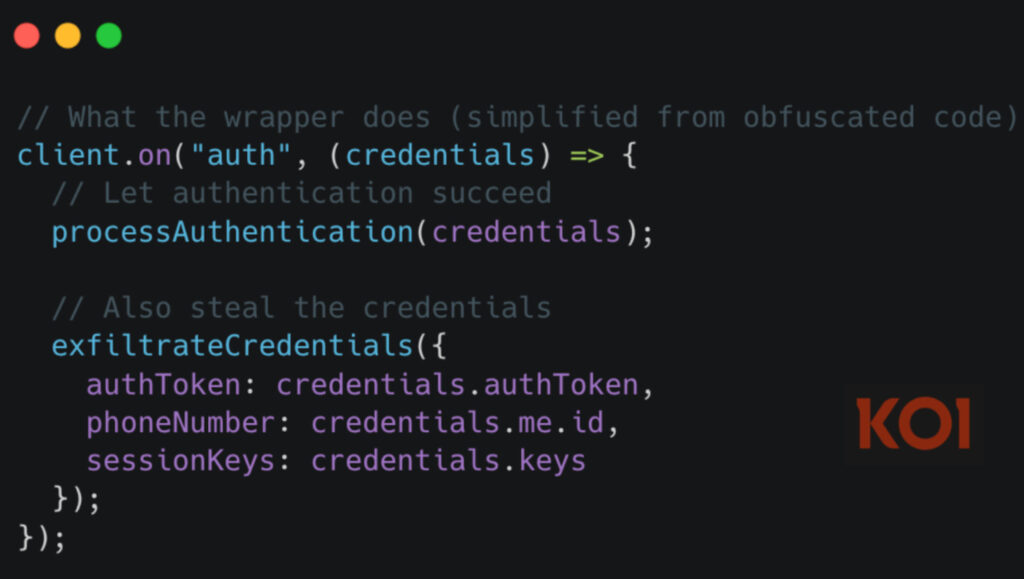
Unlike many malicious NPM packages that rely on typosquatting or fail to function properly, lotusbail maintained the core functionality of the Baileys library, enabling applications to send and receive WhatsApp messages via WebSocket, except it did so while quietly wrapping this functionality with code that intercepted and stole all traffic.
As soon as a developer authenticated through the library, the package captured WhatsApp credentials, including session tokens and pairing codes. Every message sent or received, past and present, was logged and prepped for exfiltration. This included text messages, media files, and full contact lists with associated phone numbers.
Koi Security
The data was then encrypted using a custom RSA implementation. While WhatsApp natively supports end-to-end encryption, this additional cryptographic layer was designed to conceal the exfiltrated data from network monitoring tools.
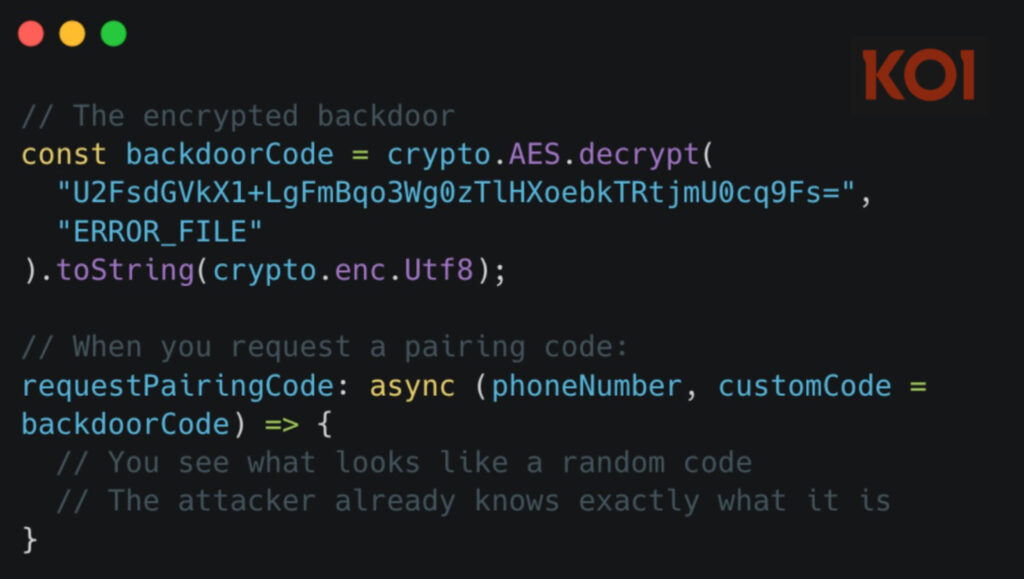
Perhaps the most insidious feature was the package's exploitation of WhatsApp's device pairing mechanism. The malware embedded a hardcoded, AES-encrypted pairing code that silently linked the threat actor's device to the victim's WhatsApp account. This pairing provided persistent backdoor access, remaining active even after the malicious package was removed.
Koi Security
In effect, uninstalling the lotusbail package does not sever the threat actor's connection. Victims must manually unlink all devices through WhatsApp's own settings to fully cut off access.
The attack exploited a growing trust gap in open-source software ecosystems, particularly where functionality masks malicious intent. NPM, a critical component of JavaScript development, remains a high-value target for supply chain attacks due to its broad adoption and ease of distribution.
Developers who unknowingly integrated lotusbail into their projects may have already exposed end-user data and compromised organizational security. Coders are recommended to audit installed dependencies for suspicious behavior and monitor app behavior at runtime for signs of unauthorized data access or unexpected network activity. Those affected should manually unlink all devices from WhatsApp accounts via in-app settings to revoke any malicious persistent access.







Leave a Reply