
A leak of internal Intellexa documents revealed new technical details about the Predator spyware platform, including covert mobile infection techniques that exploit advertising networks and mobile radio protocols.
Despite mounting sanctions and investigations, the company remains active across multiple countries and continues to develop advanced surveillance capabilities.
The investigation, led by Inside Story, Haaretz, and the WAV Research Collective with technical analysis by Amnesty International’s Security Lab, exposes the most detailed picture yet of Intellexa’s spyware ecosystem, infrastructure, and internal practices.
Zero-click infections via ads
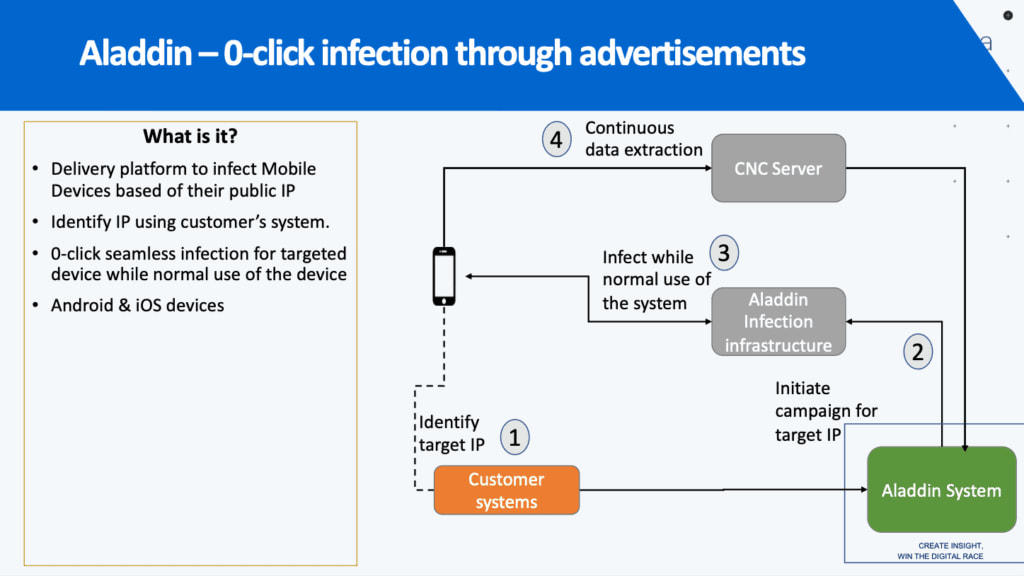
The most alarming revelation is the existence of Aladdin, a “remote zero-click” delivery vector that abuses the online advertising ecosystem to infect mobile devices without any user interaction. Internal documentation shows that Aladdin embeds exploits inside malicious digital ads, which can be served via legitimate websites or apps. Simply viewing the ad is enough to trigger an infection.
The system relies on public IP addresses or ad-related identifiers to target users. Attackers can instruct ad platforms (via DSPs) to deliver the malicious payload to specific devices, effectively turning the global ad tech supply chain into a spyware delivery mechanism. Amnesty and Recorded Future found infrastructure and corporate links tying Intellexa to multiple ad-related front companies used to operate Aladdin.
Amnesty International
Recorded Future’s Insikt Group mapped a sprawling corporate network supporting Predator operations, including front companies in Czechia, the UAE, and Greece. Two companies, Pulse Advertise and MorningStar TEC, appear linked to the Aladdin ad-based delivery system.
Aladdin has reportedly been active since at least 2024 and remains in use in 2025.
Samsung exploit
Another newly confirmed vector is Triton, a baseband exploit targeting Samsung Exynos chipsets via fake 2G base stations. Delivered through localized tactical hardware, Triton exploits radio communication layers, allowing Predator to infect nearby devices without user action.
While its current use status is unclear, leaked technical documentation and training materials confirm the existence and design of the attack, previously suspected by Amnesty researchers. This method would allow operators to infect devices without relying on phishing or network injection, useful in high-security or low-connectivity environments.
Remote access to “air-gapped” spyware systems
Leaked training videos also show Intellexa support staff remotely accessing live Predator systems deployed by government customers. Using TeamViewer, Intellexa employees could view operational dashboards, access logs, and, in some cases, interact with components that store sensitive surveillance data.
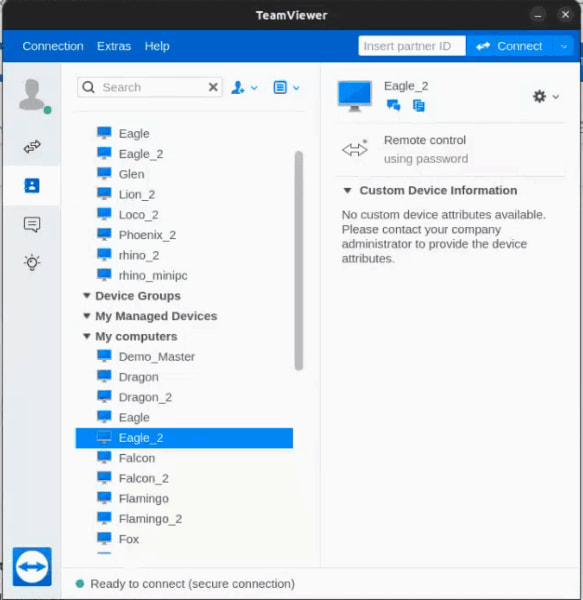
This contradicts claims made by other spyware vendors that they have no access to client operations post-deployment. In one example, Intellexa staff connected to a live system used in Kazakhstan, observing real-time logs of failed infection attempts and accessing backend interfaces normally reserved for government operators.
The revelations add legal liability complexities. If Intellexa has access to the data collected by its clients, often against activists and journalists, it may be directly complicit in surveillance abuses.
Zero-day exploits
Intellexa continues to lead in the exploitation of zero-day vulnerabilities across Android and iOS platforms. Google’s Threat Intelligence Group attributes at least 15 zero-days to the company since 2021, covering remote code execution (RCE), sandbox escapes, and privilege escalation.
These exploits were used in campaigns worldwide, including a 2025 Predator attack against a human rights lawyer in Pakistan’s Balochistan region. Google also identified Predator targeting hundreds of accounts across countries such as Kazakhstan, Angola, Egypt, Saudi Arabia, and Uzbekistan.
For iOS, Intellexa uses a modular framework called JSKit, obtained from an external exploit broker and shared across multiple vendors. Its Android exploitation uses a custom V8 exploit framework tied to several known Chrome vulnerabilities.

Amnesty International
Despite US sanctions and ongoing criminal trials in Greece over Predator’s use in the “Predatorgate” scandal, Intellexa continues to shift infrastructure, obscure its ownership, and adapt technically to maintain global operations.
The findings demand urgent responses from platform vendors, regulators, and the advertising industry to contain a threat that is becoming stealthier, more scalable, and increasingly difficult to detect.
Users are recommended to keep their devices up to date, use Lockdown Mode on iOS and Advanced Protection on Android, block ads and ad tracking where possible, and monitor app activity on the device.







Leave a Reply