
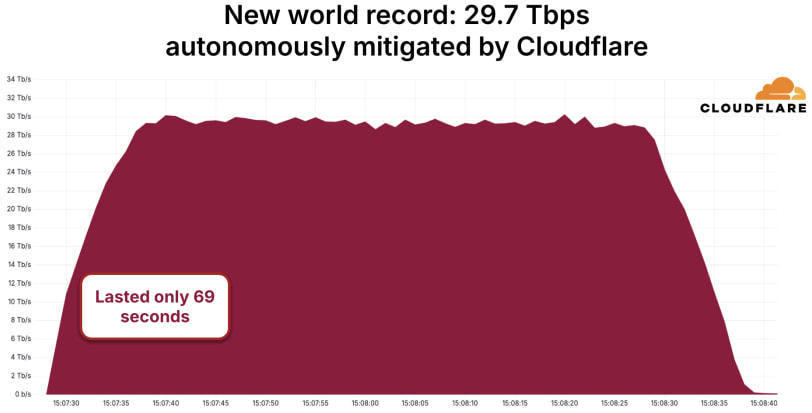
The Aisuru botnet set a new record for the largest Distributed Denial-of-Service (DDoS) attack, unleashing a 29.7 Tbps UDP flood in October 2025.
Cloudflare, which detected and autonomously mitigated the attack in just 69 seconds, confirmed the incident in its Q3 DDoS threat report, marking a 707% year-over-year increase in attack size.
The attack, characterized by a high-volume UDP carpet bombing technique, targeted an average of 15,000 destination ports per second and was designed to bypass conventional defense systems by randomizing packet attributes. Cloudflare's global network, leveraging BGP anycast and automated filtering, absorbed the full brunt of the attack traffic, which originated from infected devices across 113 countries.
Cloudflare
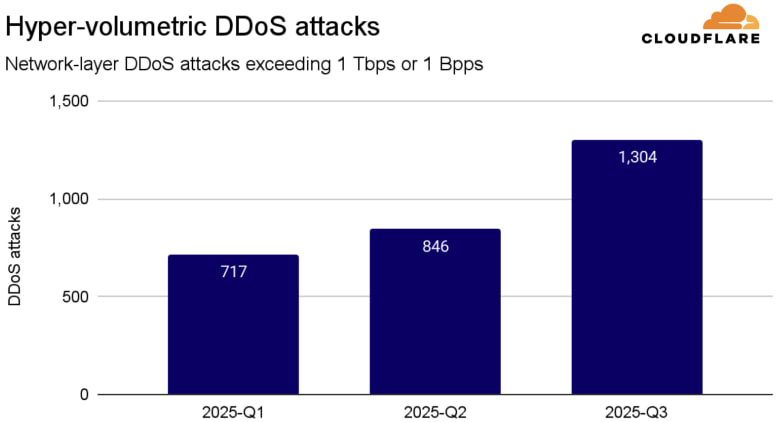
The 29.7 Tbps assault came just weeks after a previously reported 22.2 Tbps attack in September, also mitigated by Cloudflare and suspected to be linked to Aisuru. In Q3 alone, Cloudflare recorded 1,304 hyper-volumetric attacks from the Aisuru botnet, a 54% increase over the previous quarter. Aisuru now controls between 1 and 4 million infected hosts globally and has become the dominant player in the current DDoS ecosystem.
The botnet is distributed as a service-for-hire, allowing anyone with modest resources, a few hundred to a few thousand US dollars, to launch attacks that can overwhelm core internet infrastructure. This commoditization of massive-scale attacks significantly lowers the barrier for nation-state proxies, hacktivists, and cybercriminals to conduct impactful operations.
Aisuru's operations have already led to unintended disruptions in the United States, even when ISPs were not the intended target, according to Cloudflare. When botnet traffic saturates backbone links, even critical infrastructure like emergency services and healthcare systems could be indirectly affected.
Cloudflare
Targets of Aisuru-driven attacks span a wide range of sectors. In the United States, telecommunications tops the list, while other countries have seen different sectors hit hardest. The report mentions gaming in Germany, banking in Austria, retail in Canada and France, and cybersecurity firms in the UK. The botnet's attack patterns are tailored to each region's strategic industries.
Broader DDoS landscape
Beyond Aisuru, the Q3 2025 threat landscape showed a sharp geopolitical correlation. Mass DDoS attacks coincided with political unrest in the Maldives, France, and Belgium, where nationwide protests and strikes were mirrored by surges in cyberattacks.
Meanwhile, DDoS attacks targeting AI companies surged by 347% month-over-month in September, driven by rising public scrutiny and government investigations into generative AI regulation in the UK and EU.
One of the more startling metrics in the report is the 31,900% increase in HTTP DDoS traffic originating from Indonesia since 2021. Indonesia has maintained its position as the #1 global source of DDoS attacks for over a year, reflecting both the country's growing footprint in the IoT device ecosystem and the challenges of securing consumer-grade hardware.
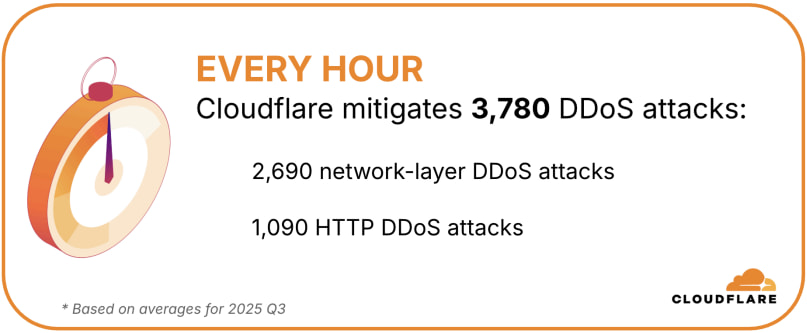
The evolving scale and speed of modern DDoS attacks render traditional mitigation methods obsolete. Many scrubbing center-based solutions lack the ingress capacity to even detect, let alone absorb, attacks peaking above 20 Tbps. In Q3 2025, Cloudflare mitigated an average of 3,780 DDoS attacks per hour, with 71% of network-layer attacks ending in under 10 minutes, far too fast for manual response or on-demand activation.
To defend against this new wave of volumetric threats, organizations should avoid relying solely on on-premise appliances or scrubbing centers with limited bandwidth, and implement always-on, globally distributed mitigation solutions capable of automatic response at terabit scale. Also, harden network infrastructure by blocking unnecessary UDP traffic, enforcing rate limits, and deploying behavior-based anomaly detection.







Leave a Reply