
MuddyWater, an Iran-aligned threat actor, has been targeting critical infrastructure in Israel and Egypt using a novel spyware called MuddyViper.
The operation, active between September 2024 and March 2025, was uncovered by ESET researchers, who analyzed previously undocumented malware, refined techniques, and increased operational maturity from a group historically known for noisy, unsophisticated intrusions.
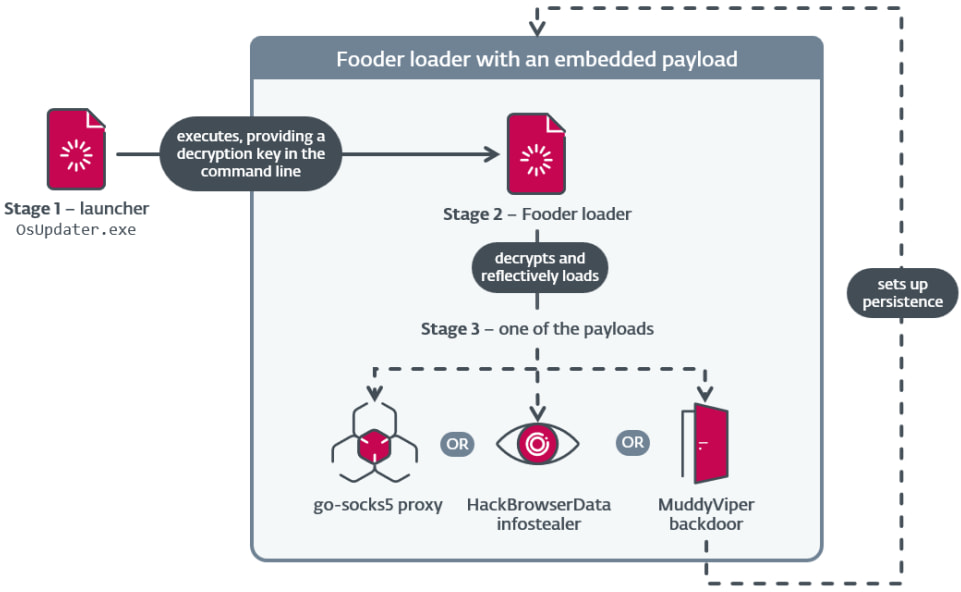
At the heart of the campaign is a new loader-backdoor combo including the Fooder loader and the MuddyViper backdoor. Fooder, a C/C++ loader, masquerades as a classic “Snake” game and features a custom delay function designed to evade automated sandbox analysis by mimicking game logic and introducing execution delays. Once launched, Fooder reflectively loads MuddyViper directly into memory, avoiding disk writes and standard detection mechanisms.
ESET
MuddyViper provides full remote control capabilities to attackers. It can collect system and browser data, steal credentials, launch reverse shells, and persist via registry keys or scheduled tasks. Notably, it uses verbose logging and a hardcoded list of over 150 process names to monitor the presence of security tools.
Communication with command-and-control (C&C) servers occurs over HTTPS, with data encrypted using AES-CBC via the Windows Cryptography API: Next Generation (CNG), a rarity among Iranian APTs and unusual across the threat landscape.
Beyond MuddyViper and Fooder, the campaign deployed an arsenal of custom and adapted tools:
- CE-Notes: A browser-data stealer focused on Chromium browsers, storing data locally in ce-notes.txt. It mimics GitHub's ChromElevator and circumvents Chrome's app-bound encryption.
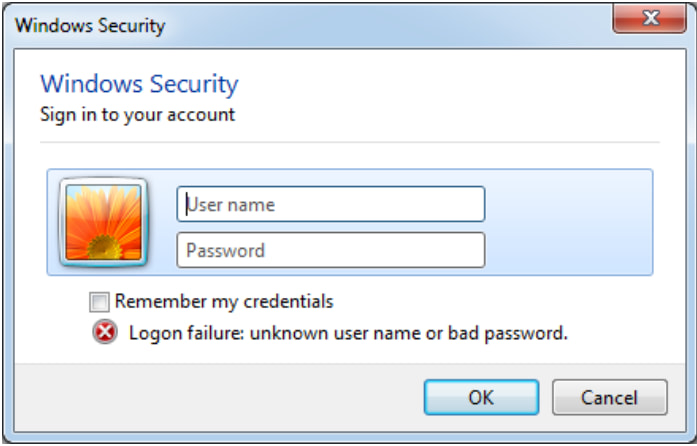
- LP-Notes: A credential harvester using a fake Windows Security dialog to trick users into revealing login details. It stores encrypted credentials in lp-notes.txt.
- Blub: A cross-browser data stealer with support for Chrome, Firefox, Edge, and Opera. It decrypts and extracts stored credentials, saving them in plaintext.
- gosocks5 reverse tunnels: Go-based proxy tools used for stealthy C&C routing and lateral movement. These tools were often embedded within Fooder payloads and continue to be a mainstay in MuddyWater operations.
ESET
Targeting focus
MuddyWater has been active since at least 2017 and is linked to Iran's Ministry of Intelligence and Security. The threat actors' primary targets in this operation included engineering, government, manufacturing, utilities, and academic organizations in Israel, alongside a single technology firm in Egypt. Interestingly, one of the utility-sector victims had previously been compromised by Lyceum, another Iran-aligned group. This suggests potential collaboration or operational handoff, a theory reinforced by observed cooperation between MuddyWater and Lyceum in January and February 2025.
In that joint sub-campaign, initial access was gained via spearphishing that delivered Syncro RMM software. MuddyWater later installed PDQ Deploy and a Mimikatz loader disguised as a certificate file, likely handing control to Lyceum post-access, indicating a possible role for MuddyWater as an initial access broker.
ESET warns that despite traces of operational immaturity, the campaign's success in evading detection for months signals an urgent need for enhanced vigilance and cross-sector information sharing.







Leave a Reply